Editorials All posts
The Rebirth of Linux
There were quite a few words on the death of Linux on the desktop lately, ...
5 Technologies That Will Make Your Bad Habits Less Unhealthy
For one reason or another a lot of us have a vice or two, a ...
Earn Money for Your Favorite Charities by Switching from Google to Goodsearch
If you search using GoodSearch, the company will donate 50% of the revenue they earn ...
Networking All posts
ISDN Modem
ISDN – otherwise known as integrated services digital network – is a digital phone connection ...
Electronics All posts
Mobile Satellite Service
Mobile Satellite Service (MSS) is a type of mobile telephone service that depends on portable ...
IT Management All posts
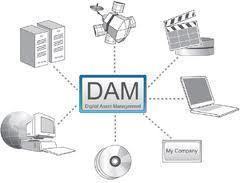
Digital Asset Management
Digital asset management (DAM) is the technology that allows organizations or individuals to manage both ...
Mobile Telephony All posts
AMPS (EIA/TIA-553) and NAMPS (IS-91)
Mobile Frequency Range Rx: 869-894; Tx 824-849 Multiple Access Method FDM Duplex Method FDD Number ...
Microsoft Windows All posts
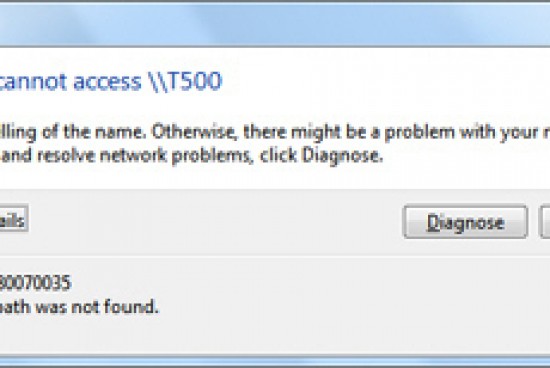
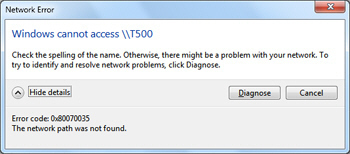
0x80070035
As the number of home computer users creating local networks increases, so does the number ...
Wireless Networks All posts
802.11g
802.11g is one of the standards used for high speed wireless networks, commonly known as ...
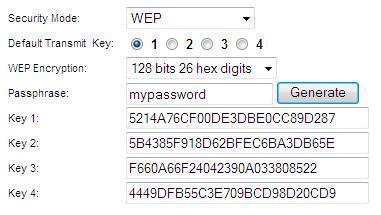
WEP Key Passphrase
A wireless network key is an encryption key for that prevents unauthorized users from accessing ...
How to Change WEP to WPA
Changing WEP to WPA is a great way to increase a wireless network’s security. These ...
Passwords All posts
How to Recover a Zip Password
PKZip utilizes a proprietary stream cipher that is vulnerable to a known plaintext attack, as ...
How Does RAR Password Recovery work?
RAR Password Recovery is a password recovery software that is specifically designed to recover lost ...
Netscape Navigator Stored Password Recovery
Netscape Navigator stores usernames and passwords for web sites which you have logged in to. ...