Radio-Frequency Identifier (RFID) technology has become really popular because of the various advantages it comes with. However, such as passports, national identity cards, credit cards etc have become a serious security concern. Two electrical engineering students (Ilan Kirschenbaum and Avishai Wool) from Tel Aviv University wrote a paper titled "How to Build a Low-Cost, Extended-Range RFID Skimmer." The paper demonstrates just how very simple it has become to 'skim' the RFIDs in your office key or car key. An RFID skimmer can therefore be loosely defined as a device that is used to collect mass information from RFID systems.
An RFID skimmer is used to collect legitimate information such as controlling inventory in supermarkets or pharmacies. However, sometimes the RFID skimmer can be used to collect illegitimate information thus causing a security breach. The device can be used by identity thieves as part of a relay attack system where the attacker uses the victim's information to for example make purchases or start a car. Crimes of theft and fraud using an RFID skimmer are therefore very easy to commit.
How an RFID Skimmer Works
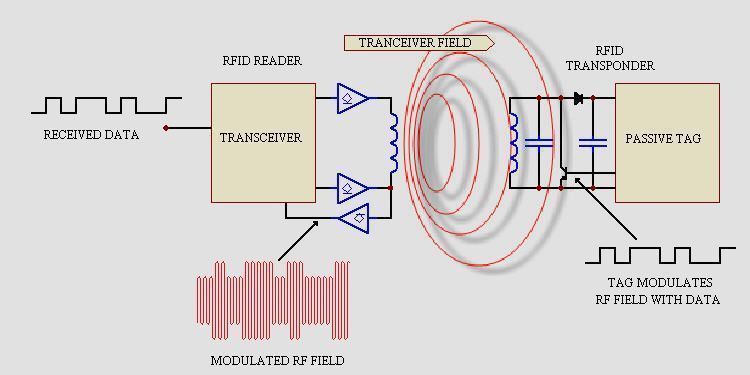
It is quite easy to build a low cost, portable, high powered RFID skimmer. In their paper, Kfir and Wool described a relay-attack on an RFID system that violates the implication that the RFID tag must touch the RFID reader at a range of 5 – 10 cm. Their system architecture involves two devices, a “leech'' and a “ghost'', that communicate with each other. The RFID skimmer was able to read ISO-14443 tags from a distance of approximately 25cm, used a lightweight 40cm-diameter copper-tube antenna, and was powered by a 12V battery. An RFID skimmer application can run on a small laptop or a mobile phone connected to an RFID reader. Any sounds and images will then be recorded from a nearby webcam.
An RFID skimmer signals RFID tags within its vicinity and then records the responses. Depending on its power, it can pick up signals in a wide radius and surreptitiously read the contents of simple RFID tags.
Users are therefore advised to be careful with the information that they hold with RFID tags so as not to expose sensitive information to willing 'wrong hands'.
Security Breaches using an RFID Skimmer
- Thieves can collect information from your wallet without your knowledge.
- Thieves can hack information from your VISA, MasterCard or American Express RFID credit card from as far as a foot away. The RFID reader is used to obtain the full name of the card holder, the credit card number and the expiration date. If this information can be read, then this means that the card can be cloned in a matter of seconds and someone else can pass themselves off as you. They can use your card to make unauthorized purchases.
- An RFID skimmer can be used to read your car key RFID tag. The user then tricks the car into unlocking and speeds off with the car. This theft is unique by the fact that no sign of forced entry can be seen.


jrgc
where can i get one of these card readers/skimmers
albert holguin
hello, i need someone to build a long range low cost rfid skimmer for me