In the study of cryptography the terms plaintext and ciphertext are used to describe the plain language message or information and the resulting encrypted message or data that results from the use of a cipher or encryption algorithm. The resulting ciphertext is not readable by either a human or computer without the correct cipher to decrypt the information. In order to decipher the text, the correct key and decryption method must be employed or else the information contained in the encrypted message will not be usable.
What is Plaintext?
Plaintext is the term used to refer to the information in plain language that the sender desires to send to one or more receiving computers or individuals. Also referred to as cleartext, plaintext is commonly referred to as the input to a cipher or encryption algorithm. The term cleartext can also refer to sounds, images, or other multimedia information that is transmitted without encryption. In laymen’s terms, plaintext refers to information that is represented in its “normal” form before any action is taken to conceal or compress the data.
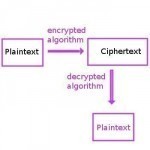
In cryptographic circles, plaintext is commonly used as the input to a cipher or encryption algorithm. The output of these cipher’s is normally referred to as ciphertext. The outputted text can be a result of one or many rounds of encryption employed on the plaintext depending on the specific algorithm in use.
What is Cryptanalysis?
The study of methods used to obtain the true meaning of encrypted information without access to the data is referred to as cryptanalysis. Most of the time, this study requires knowing how the cipher that created the encrypted communication works and determining a method to guess or determine the secret key used for the encryption. Also referred to as codebreaking, cryptanalysis became famous in modern history during World War II when the United States and the Allied Powers were able to obtain significant tactical and strategic advantage over the Axis powers by breaking their respective codes. Since ciphertext is normally the easiest part of any cryptosystem to acquire, it is one of the most important components of cryptanalysis.
The Importance of Plaintext Handling
Even the strongest cipher in the world cannot withstand weak or insecure handling of large amounts of plaintext. In the worst case, these actions allow attackers to simply bypass the cipher altogether. Plaintext messages are vulnerable both when used, in storage, or in paper or electronic format. Organizational focus on physical security programs are key to avoid weaknesses in an encryption system due to poor physical security practices. Additionally, attackers have been known to conduct “dumpster diving” in order to obtain plaintext information that can either be used to directly obtain secrets or to help conduct a brute force attack against any given computer system.
Simply improving the physical security of the trash is not sufficient to guard against theft of plaintext. In today’s world, most plaintext is stored digitally and is open to theft via portable media or online hacking. As a result, implementing local procedures to guard against unauthorized removal of portable media and proper disposal of legacy disk drives and discarded computers is another key to preventing theft and possibly compromise of plaintext data that may contain sensitive or privileged information.
A continual problem is the storage of classified plaintext information on laptop computers in the United States and British governments. All major agencies have had more than one instance of laptops that contain classified information stolen from employees. Unfortunately, in most cases proper laptop disk encryption procedures were either not employed or not yet improved before the thefts occurred. As a result, potentially sensitive information in plaintext form was exposed to unauthorized personnel.
Even in cases where the information stored on a host computer is encrypted, portable media that is used to transfer data between system is not encrypted and represents another threat to compromise of sensitive plaintext data. For example, in the fall fo 2007, Her Majesties Revenue and Customs office “lost” CD/DVDs that contained a minimum of 24 million child benefit recipients in the United Kingdom…unfortunately for the UK citizens and residents, none of the information on the discs was encrypted! .
What are the Types of Ciphers?
In order to understand modern-day ciphers, it’s worth taking a look at a number of the well-known historical ciphers throughout history preceding the modern day. Today, historical ciphers are not normally used for standalone encryption since they can be cracked easily through modern brute force attacks or by analyzing simply the ciphertext. Modern-day methods have improved to the point that all methods but the one-time pad can be cracked with only access to the ciphertext.
Pen and Paper Ciphers
These types of cipher are also known as the “classical ciphers” and include the following methods:
Substitution cipher
In the substitution cipher, plaintext characters or units are replaced directly with cipher text. Famous instances of this cipher include the One-time pad and the Caesar cipher.
Transposition Cipher
In the transposition cipher, the resulting cipher text is a permutation of the plaintext input. A famous example of this type of cipher is the Rail fence cipher.
Polyalphabetic substitution Cipher
In the polyalphabetic substitution cipher, multiple substitution alphabets are used to create ciphertext from the plaintext input. Famous examples of this cipher include the Vigenère cipher and Enigma machine from WW2.
Permutation cipher
The permutation cipher is a transposition cipher where the key to the ciphertext is a permutation.
How Do Modern Ciphers Work?
Current-day ciphers are significantly more secure than the classic cipher techniques. They are created to be able to withstand a variety of attacks on the ciphertext. Attackers are not able to determine what the key(s) used in modern ciphers are even with access to a significant amount of plaintext and corresponding ciphertext. The modern day cipher techniques include:
Private-key Cryptography
In private key cryptography which uses a symmetric key algorithm, the same key is used to both encrypt and decrypt information.
Public-key Cryptography
In public key cryptography that uses an asymmetric key, there are two key used for encryption and decryption.
For ciphers that leverage symmetric key algorithms (including AES and DES), both the sending and receiving computer and host has to have a shared key setup in advance. The key must be kept secret from all other users in order for the communication sessions to remain private. The sending computer will use the secret key for encryption and the receiving computer uses the same key to decrypt the ciphertext to plaintext.
For asymmetric key ciphers such as RSA, there are two separate keys used for operations. A public key is promulgated that allows any sending computer to encrypt data. The private key is only held by the receiving party and allows only that person, computer, or authorized user to decrypt the information.
For symmetric key ciphers, the two variants in use today are stream and block ciphers. Stream ciphers encrypt information or plaintext data one unit or character at a time while processing a continual stream of data. The transformation of the information will vary during the encryption process based on the specific encryption process being employed. For block ciphers, fixed-length groupings of data called blocks are processed using a transformation calculation.
Cryptanalysis Attack Models
There are a number of cryptanalysis attack models in use today for attempting to crack or break cipher texts. Some of the most common include: ciphertext-only, batch chosen, chosen-chiphertext, and the related-key attack.
Ciphertext-only Attack
In the ciphertext-only attack, the cryptanalyst can only gain access to code or ciphertexts.
Known-plaintext Attack
In the known-plaintext attack, the individual or group conducting the attack only has access to a group of ciphertexts where he or she knows the corresponding plaintext.
Chosen-plaintext Attack:
In the Chosen-plaintext attack, the attacker is only able to obtain the ciphertexts that correspond to a random or arbitrary set of plaintexts of his or her choosing.
Batch Chosen-plaintext Attack
In the Batch Chosen-plaintext attack, the attacker is able to choose all of the plaintexts prior to any of them being encrypted.
Adaptive Chosen-Plaintext Attack
In the Adaptive Chosen-Plaintext attack, the cryptanalyst is able to create a set or series of interactive queries. During these queries, he or she is able to choose subsequent plaintexts that are based on the information from the previous encryptions.
Chosen-Ciphertext Attack
During the Chosen-Ciphertext attack, the person or group conducting the attack is able to obtain the plaintexts that correspond to a random set of ciphertexts of their choosing.
Related-Key Attack
In the related-key attack, the attacker takes an approach similar to a chosen-plaintext attack. The exception is that the attacker is able to get access to ciphertexts that are encrypted under two different keys. The keys are not known; however, the relationship between the two is known by the attacker.
What is the Known Plaintext Attack?
KPA, or the known plaintext attack, is a well-known attack model in cryptanalysis where the attacking party has a good ample size of the “crib” or plaintext as well as the ciphertext. This information can be used to help identify information such as secret or private keys or code books. The original theory behind a “crib” was that if a cryptologist was able to have a recommendation or idea about how ciphertext can be translated to plaintext, then the person or team would have a “wedge” or a test to help break the cipher. When running tests, if the engineers were able to see some words appear, then the settings being used to break the code might be tweaked to decrypt an entire message.
Cracking the German Enigma System
During World War 2, the German High Command was very conscious regarding the security of the Enigma Cipher system. They were fully aware of the issue or problems of cribs; however, the daily operators of the system were not quite as careful was they should have been. For example some of the plaintext of messages transmitted from the field was able to be guessed by the Bletchley Park Team due to the time of day that the message was sent (weather messages were one good example being sent at the same time every day). Even standard reports that were routine such as “Nothing to report” from the German Africa Corps helped Allied cryptologists work to crack the Enigma code.
At Bletchley Park in World War II, significant effort was expended to force the German military to send messages with known plaintext by the Allies. As an example, when the Allied analysts needed more material to work with, they would ask the Royal Air Force to bomb or “seed” certain areas in the North Sea with mines. When the resulting German Enigma messages were transmitted, they were assumed to contain the name of the harbor or area threatened by the mines.
Later in the war, a capture German did reveal under British interrogation that the Nazis had instructed all Enigma operators to spell out numbers to help further encode them. Alan Turing was then able to review decrypted messages and assess that “One” in German, “eins” was the most common string in the Enigma plaintext. He was able to automate the crib” process which resulted in the “Ens Catalogue.” This work included all possible settings and keysettings of the German Enigma machine.
Similarly, the Polish Cipher Bureau was able to leverage cribs in the “ANX method” prior to WW2. This came from the German use of “ANX” which is German for the word “to” with an “X” used as a spacer.
Plaintext Attacks with Modern Ciphers
The modern ciphers in-use by governments and industries today are not susceptible to the known-plaintext attacks of the past. This is primarily due to the advances made in the study of cryptography and lessons learned from World War 2.
There are cases of ciphers in-use today that are open to this attack. For example, the PKZIP stream cipher that is used by older specifications of the Zip format specification can be attacked using the known plaintext method. If the zip file is encrypted using AES; however, it is not susceptible to the attack.


alemie
how to convert the WOBBIHWAC encrtion to decryption text(plain text)?