SHA stands for Secure Hash Algorithm. It consists of five hash functions designed by the National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST). The five algorithms are SHA-1, SHA-224, SHA-256, SHA-384, and SHA-512. SHA-1 is the most commonly used of the SHA series.
Hash algorithms are called secure when
- It is impossible to find a message that corresponds to a given message digest.
- It is impossible to find two different messages that produce the same message digest.
- If a message is changed even by a single character, the result will be a completely different message digest.
SHA-1 has these properties and is therefore referred to as secure. It is designed to work with the Digital Signature Algorithm (DSA). SHA-1 is a one-way hash function. One-way functions are characterized by two properties. The first is that they are one-way. This means that you can take a message and compute a hash value, but you cannot take a hash value and recreate the original message. It is also collision-free and, thus, no two messages can hash to the same value.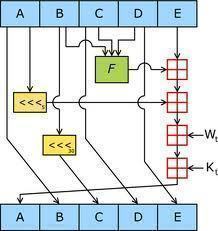
SHA-1 produces a 160-bit message digest with a maximum length of 264 ?1. The message M to be hashed must have a length of l bit, where 0 l 264. The message digest is the fixed-length output of a message. The message digest is then input to the DSA, which will then generate the signature for the message. Signing the message digest instead of the message offers improved performance because the message digest will be much smaller than the message. The recipient of the message will then use the same hash algorithm to verify the signature. Any change that occurs during transit will result in a different message digest and, thus, the signature will not verify. Once it is verified as true, the recipient is able to unlock the message. This method prevents unauthorized users from viewing messages that are not intended for them.
When computing a message digest, SHA-1 processes blocks of 512 bits. The total length of the message digest will be a multiple of 512. This process is known as padding of the message.
SHA-1 differs from SHA-0 only by a single bitwise rotation in the message schedule of its compression function.
Cryptanalysis is the method of obtaining encrypted information without using the hash value. Breaking a hash function implies showing that the one-way property does not hold for it. Cryptographers have demonstrated that it just might be possible for the SHA-1 hash algorithm to be broken. Some have presented a collision for 58-round SHA-1, found with 233 hash operations. A brute force search would require 280 operations. However, experts argue that this might not happen for some time. Nevertheless, attacks always get better, and the National Institute of Standards and Technology (NIST) already has standards for longer – and harder-to-break – hash functions: SHA-224, SHA-256, SHA-384, and SHA-512.
Applications of SHA-1
SHA-1 can be used in a variety of applications:
- Security applications that require authentication
- Electronic funds transfer
- Software distribution
- Data storage

Follow Us!