The 802.11i wireless standard was released by the IEEE on June of 2004 and implements improved encryption for wireless networks than realized on past standards released. Commonly referred to as the WPA2 implementation, the 802.11i implementation requires newer encryption standards than seen with the WEP implementation by requiring TKIP (Temporal Key Integrity Protocol) and AES (Advanced Encryption Standard) use. Networks implementing a pure form of the 802.11i standard deprecate the use of the less-secure RCA stream cipher.
What Improvements Does the 802.11i Standard Feature?
The improvements to wireless security realized in the 802.11i wireless standard satisfy a much higher level of security commonly required by national and state-level government agencies. In order to support the higher standard through leveraging AES encryption, WiFi networks are required to upgrade the underlying infrastructure to support the dedicated hardware that AES requires. After making these upgrades; however, the key caching feature of 802.11i supports a fast reconnection to the wireless server for users who go offline for a short time-frame as well as pre-authentication. The pre-authentication feature supports advanced wireless applications which use VoIP (Voice over Internet Protocol).
History of Wireless Networking Standards
The IEEE has been the organization responsible for developing and releasing guidance for standard implementations for wireless networking since the 1990s. The organization is responsible for wireless communication implementation in the 2.4, 3.6, 5, and 60 GHz frequency bands under the guidance of the IEEE 802 Committee (IEEE LAN/MAN Standards Committee). The original version of the standard was released in 1997 and continues to be improved upon as requirements in industry dictate.
802.11 (Legacy)
The first version of the IEEE wireless standard (802.11) was first released in 1997. Later clarified in 1999, the work required a data throughput of 1-2 megabits per second and included forward error code correction. There were three physical layer technologies supported by the standard (alternative implementations); however, the legacy standard is now deprecated and no longer supported by industry.
802.11a
First released in September 1999, the 802.11a wireless standard supported an average throughput in the 20+ Mbit/second range. Working in the 5 GHz RF (radio frequency) spectrum, the 802.11a standard was susceptible to interference issues and had a smaller, overall range when compared to the 802.11B standard.
802.11b
Also released in September 1999, 802.11b features wireless operations in the 2.4GHz RF band. Although the “B” standard supports a lower overall raw data rate of 11 Mbit/s when compare to the “A” standard, it was the first implementation to see significant commercial acceptance due to significantly decreased cost of wireless networking hardware.
802.11g
The 802.11g wireless standard also operates in the 2.4 GHz frequency band. Seeing an average throughput of 22 Mbit/s, the standard also supports more advanced security options when compared to the popular, “B” implementation as well as backwards compatibility with computers which use “B” network cards to connect to the WiFi network.
802.11i
The 802.11i standard was released on June 24th, 2004 as an amendment to the original IEEE 802.11 standard. Implementation of the standard is known as WPA2, and specifies a number of security options for wireless networks that previously relied on WEP encryption.
802.11n
In October 2009, the 802.11n wireless standard was released. Supporting operations in both the 2.4 and 5 GHz radio frequency bands, the standard supports data throughput ranging from 54 to 600 Mbits/second. Also included in the 802.11n implementation is support for MIMO (multiple-input multiple-output) antenna support.
802.11ad
The 802.11ad wireless standard was released in December of 2012 by the IEEE. Commonly referred to as the “WiGig” standard, 802.11ad supports use of the 60 GHz frequency band and features throughput speeds of 7 Gbit/second. The first wireless hardware supporting the standard is expected to be on the marketplace in the early portion of 2014.
802.11ac
Currently under review and still in draft, the 802.11ac wireless standard will result in a significant increase in multi-client support. Targeting a 1 gigbit/second goal, the standard will support operations in the 5 GHz frequency band and is scheduled for release in February 2014.
Finally a Replacement for WEP
With the release of 802.11i by the IEEE, the WEP (Wired Equivalent Privacy) specification was superseded after having a number of significant security vulnerabilities exposed. Previously, a subset of the 802.11i specification was released by the WiFi Alliance under the title of WiFi Protected Access (WPA). The full implementation of 802.11i is referred to as the Robust Security Network (RSN) or WPA2. The full implementation of the standard leverages the AES (Advanced Encryption Standard) block cypher resulting in significantly better protection than realized using the RC4 stream cipher used by WEP and WPA.
How Do the 4-Way Handshake and Group Key Handshake Protocols Work?
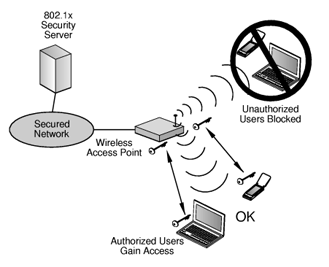
The full implementation of the 802.11i standard and Robust Security Network (RSN) includes two new protocols to network security: the 4-Way Handshake, and the Group Key Handshake. Each of the protocols leverage port access control and authentication services to both confirm and modify the applicable cryptographic keys. Within the Robust Security Network, the creation of RSNAs (Robust Security Network Associations) are permitted between stations if they have successfully authenticated or associated themselves using the 4-Way Handshake protocol. The RSN also permits use of CCMP and TKIP protocols to ensure data integrity and confidentiality within the network.
Four-Way Handshake
The Four-Way hand shake has two major requirements at the onset of the authentication process: 1 – An AP (access point) must provide valid authentication to a STA (client station), and 2 – Keys for encrypting the network traffic must be derived. Previously in the network communications process a WPA2-PSK or EAP exchange will have provided a secret shared key known as the Pairwise Master Key (PMK). Since the PMK is designed to last for an entire network session, it necessitates as little exposure as possible. As a result, the Four-Way handshake establishes another key referred to as the Pairwise Transient Key (PTK). The PTK is created by joining (or concatenating) the PMK, AP nonce, STA nonce, AP MAC address, and the STA MAC address. The resulting product is then sent through the hash function, PBKDF2-SHA1.
Another product of the Four-Way handshake is the Group Temporal Keys (GTK) which are used to decrypt broadcast and multicast network traffic.
The specific steps of the Four-Way handshake are:
Step 1 – AP sends a nonce-value to the STA (referred to as the Anonce). The client device will now have all required attributes to create the PTK.
Step 2 – STA sends its nonce value (Snonce) to the AP along with a MIC to include the required authentication which is referred to as the MAIC (Message Authentication and Integrity Code).
Step 3 – AP transmits the GTK and a sequence number along with another MIC. The sequence number is one that will be used in the next broadcast or multicast frame so that the receiving STA may perform a basic replay detection.
Step 4 – The STA transmits a confirmation to the AP.
Each of the messages are sent as EAPOL-Key frames. Once the PTK (Pairwise Transient Key, 64 bytes)is obtained, the information is divided into five separate keys:
Key 1 – 16 bytes – EAPOL-Key Confirmation Key (KCK). This key is used in 802.11i to compute the MIC on a WPA EAPOL Key message.
Key 2 – 16 bytes – EAPOL-Key Encryption Key (KEK). This key is used by the AP key to encrypt additional data sent to the client.
Key 3 – 16 bytes – Temporal Key (TK). The TK is used to decrypt or encrypt Unicast data packets.
Key 4 – 8 bytes – Michael MIC Authenticator Tx Key. This key is used to compute the MIC on Unicast Used to compute MIC on Unicast data packets transmitted by the AP
Key 5 – 8 bytes – Michael MIC Authenticator Rx Key. This key is used to compute the MIC on Unicast data packets transmitted by the station.
Note: The Michael MIC Authenticator Tx/Rx Keys used in the Four-Way handshake are only used if the implementing network is using TKIP to encrypt data.
Group Key Handshake
During a network session, the GTK used in the network may require updating due to a preset time expiration or when a client device leaves the network. This requirement is put in place to prevent the device from receiving any more broadcast or multicast messages from the AP. In order to handle the updating, the 802.11i standard defines a Group Key Handshake. This handshake works in two-ways or directions: 1 – The AP will send the new GTK to every STA in the network, and 2 – The GTK is encrypted using the KEK assigned to the STA and is protected from tampering through the use of a MIC.
The specific steps of the Group Key Handshake are:
Step 1 – The network AP sends the new GTK to all of the STAs in the network. AP encrypts the GTK using the KEK assigned to the STA and uses a MIC to protect the data from tampering.
Step 2 – The STA sends an acknowledgment for the new GTK and sends a reply to the AP.
The GTK (32 bytes) consists of three keys:
Group Temporal Encryption Key (16 bytes) – Used in 802.11i to encrypt Multicast data packets.
Michael MIC Authenticator Tx Key (8 bytes) – Used to compute the MIC for any Multicast data packets transmitted by the AP.
Michael MIC Authenticator Rx Key (8 bytes) – Not currently used.
*Note: the Michael MIC Authenticator Tx/Rx Keys are only used if TKIP is in place to encrypt network data.
Steps to Setup WPA2 Encryption on a Wireless Network
For the home or small business network administrator, making the shift from WEP to WPA2 can initially seem like a daunting task. Fortunately, if your wireless router supports WPA2 (as outlined in the 802.11i standard), it is fairly straight forward to employ the commercial-grade encryption that WPA2 provides.
Step 1 – If you are using Mac OS X, make sure you are running OS X 10.4.2 or newer (in OS X WPA2 is referred to as WPA 2 personal). On a Windows computer, if you are running Windows XP, service pack 2 or newer must be installed. If you are running a newer version of Windows, make sure you update the operating system prior to proceeding.
Step 2 – If you are running an older computer, the wireless adapter may not support WPA2. You will want to verify / update the device driver to ensure it supports WPA2. If the computer is running an Intel wireless adapter, it will need to have Intel ProSet version 7.1.4 or newer (not counting versions 8.x) to properly support WPA2.
Step 3 – Confirm that your wireless router can support WPA2. If the router has been purchased in the past year or two, it will likely support WPA2. Some routers do require you update their firmware in order to be successful with WPA2 support. Older routers will likely only support WPA and not WPA2.
Step 4 – Login to your router’s configuration panel.
Step 5 – Select the “Security” menu option and change the encryption to WPA2-AES. The specific options to locate this menu may vary across wireless router manufacturer.
Step 6 – Enter a pre-shared key in the appropriate field. You will need to note this key for future use. The key can simply be a passphrase that you can remember, but is not easy for another person to guess.
Step 7 – Configure the client computers or devices to operate on a WPA2 network by changing the network authentication mode to WPA2-PSK and entering the passphrase that you entered for the pre-shared key entry on the router setup.
Step 8 – Repeat the new configuration setup on all other client devices on your network, and it will now be configured to support WPA2.

Follow Us!