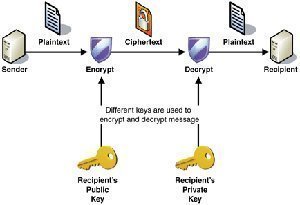
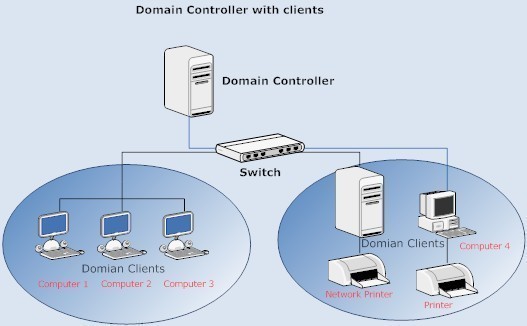
How to Enable the Windows Vista Administrator Account
In Windows Vista, there is a difference between accounts with “computer administrator” privileges and the Administrator account. In the Administrator account, the User Account Control is disabled. Also, the Administrator account is present, but hidden and disabled by default. Please be aware that Vista Beta 2 has a bug that may cause big problems, if …