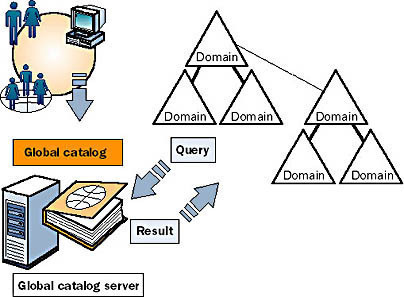
Global Catalog in Active Directory
Domains and Forests can also share resources available in active directory. These resources are searched by Global Catalog across domains and forests and this search is transparent to user. For example, if you make a search for all of the printers in a forest, this search goes to global catalog server for its query and …