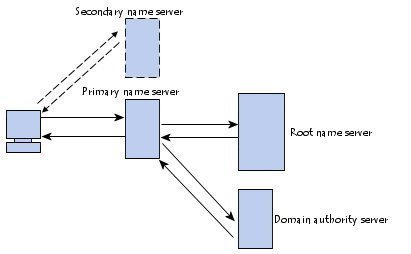
Understanding Host Name Resolution
Understanding the Purpose of Host Names In TCP/IP based networks, the packets that are transmitted over the network contain the following IP addresses: The IP address of the computer sending the packet The IP address of the destination computer intended to receive the packet. The IP address information is used to forward the packet to …