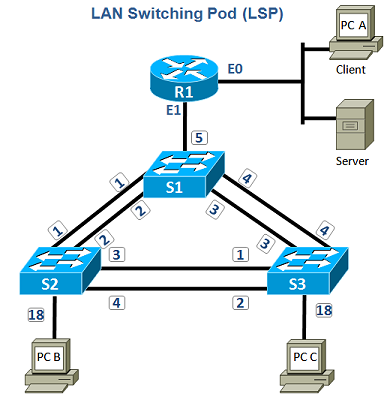
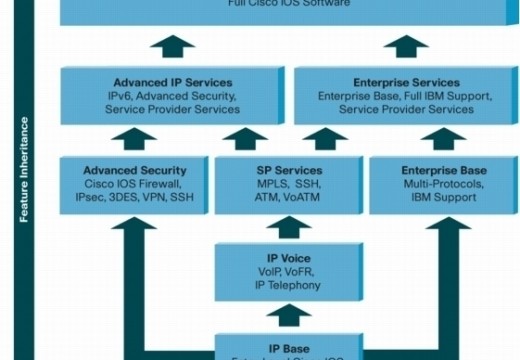
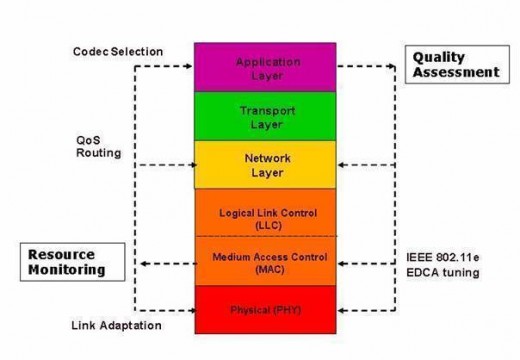
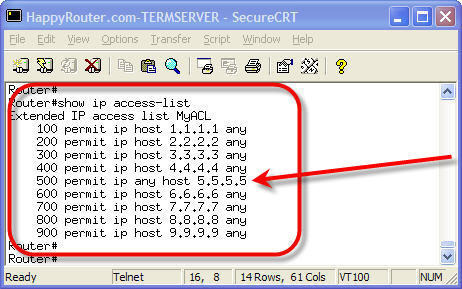
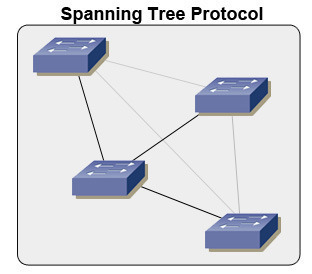
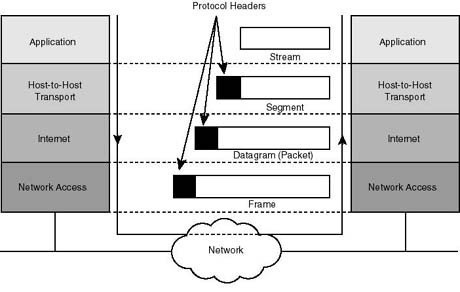
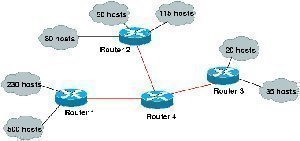
LAN Switching and Switch Types
Switches represent the features and technologies that can be used to respond to the requirements in emerging network design. Some basic operations and technologies of switches are as follows: Fast Convergence: Switches stipulate that the network must adapt quickly to network topology changes. Deterministic Paths: Switches provide desirability of a given path to a destination for certain …