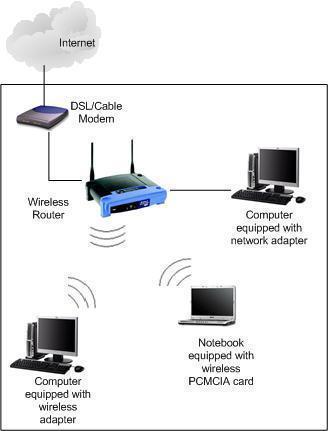
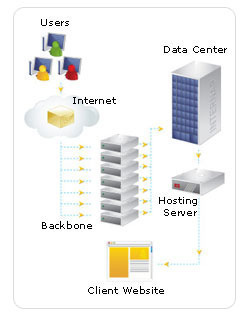
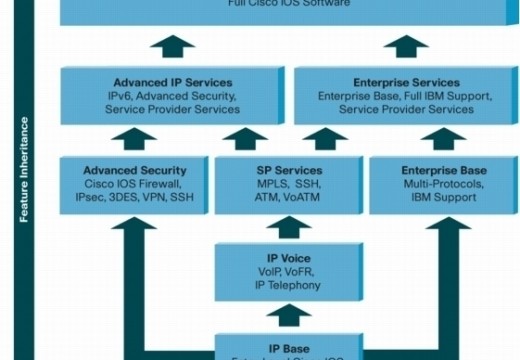
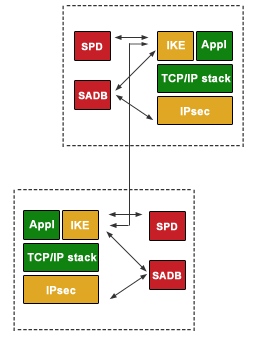
How to Use Telnet
Telnet is a utility program that allows remote access to other computers if they are installed on a network or have access to the Internet. Telnet lets users run commands on the remote computer. It can execute commands faster than the Web and other popular remote computer access applications. Telnet is not widely used as …