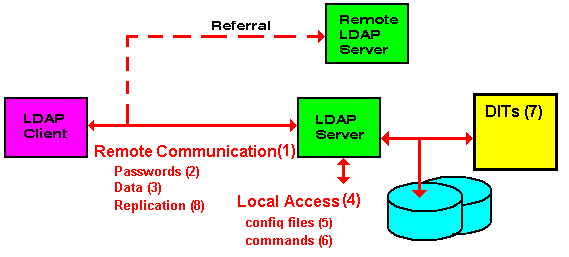
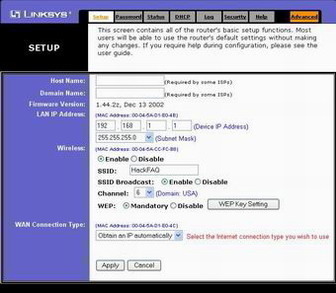
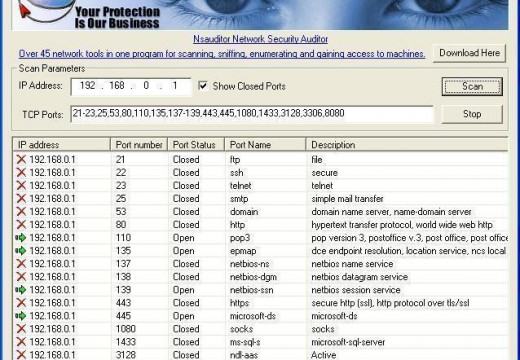
LDAP Security Issues
RFC 2829 – Authentication Methods for LDAP defines the basic threats to an LDAP directory service: Unauthorized access to data via data-fetching operations, Unauthorized access to reusable client authentication information by monitoring others' access, Unauthorized access to data by monitoring others' access, Unauthorized modification of data, Unauthorized modification of configuration, Unauthorized or excessive use of …