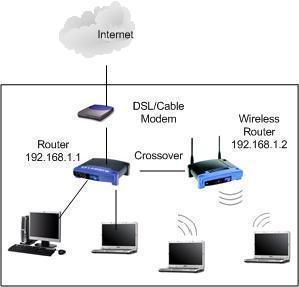
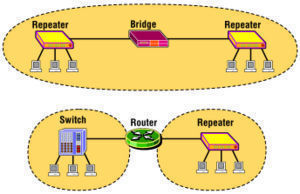
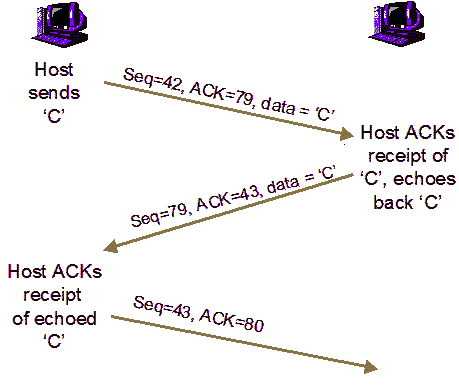
Application Layer
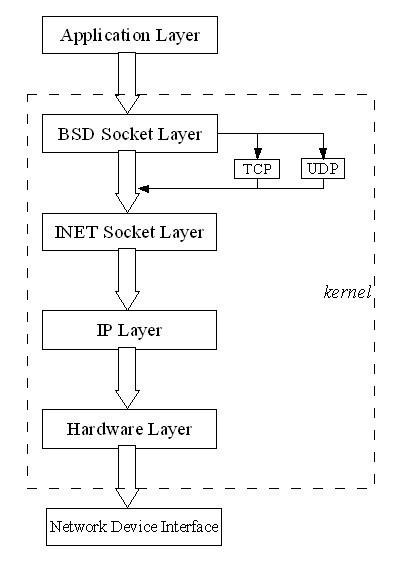
The application layer of a software is a protocol that is used for communication between a software and the network layers that it uses. The application layer allows a computer’s network to interpret requests made by the program and allows the program to interpret data from the network. Likewise, the application layer ensures that both …