How to Use Ping to Test a Network
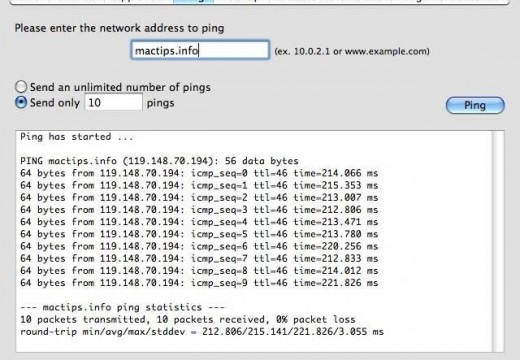
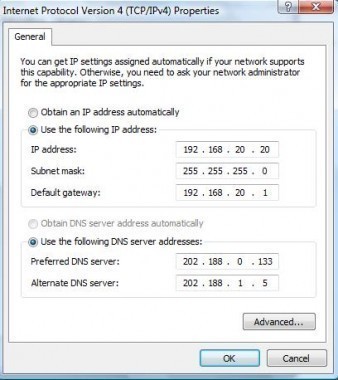
The following steps elaborate on how to use the Ping utility to perform progressively more distant tests on network connectivity. Ping the Loopback Address – Type Ping 127.0.0.1 Successfully pinging the loopback address verifies that TCP/IP is both installed and configured correctly on the local client. If the loopback test fails, it means IP stack …