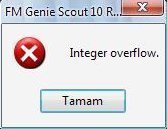
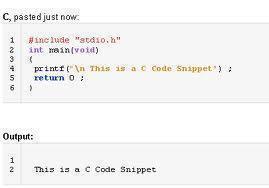
Integer Overflow
An integer overflow, or integer wrapping, is a potential problem in a program based upon the fact that the value that can be held in a numeric datatype is limited by the data type’s size in bytes. ANSI C uses the following minimum sizes: data type size (bytes) char 1 short 2 int 2 long …