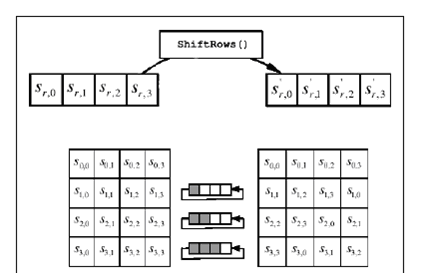
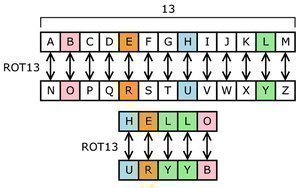
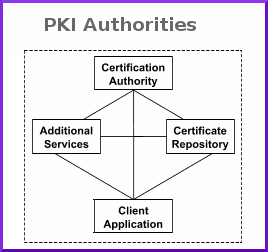
Smart Card Software
A smart card contains an integrated circuit (IC) chip containing a central processing unit (CPU), random access memory (RAM) and non-volatile data storage. Data stored in the smart card’s microchip can be accessed only through the chip operating system (COS). Smart cards provide a secure, portable platform for “any time, anywhere” computing that can contain …