The way that most services work under TCP/IP is that the server is configured to use a well known port number and the client connects from a random high port.
Most of these well known ports are port numbers below 1,024. High ports are ports 1,024 or above.
In the old days, ports below 1,024 were known as trusted ports. On Unix machines, only a user or process with root privileges is able to open an outgoing port below 1,024.
With the proliferation of Windows and single-user Unix systems, the trusted port model no longer works.
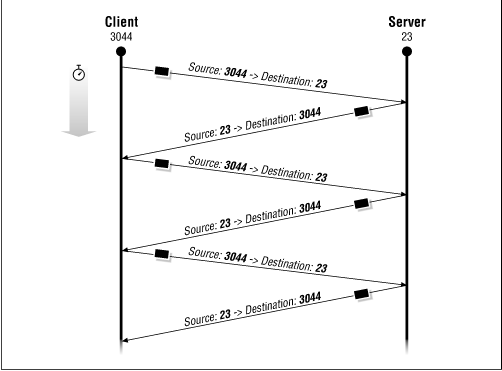
A few of the most common well known ports are:
Service Port FTP 20,21 SSH 22 telnet 23 SMTP 25 DNS 53 DHCP 67,68 TFTP 69 HTTP 80 POP3 110 NNTP 119 NTP 123 IMAP4 143 LDAP 389 HTTPS 443 IMAPS 993 RADIUS 1812 AIM 5190
The file /etc/services on most Unix machines lists the port assignments for that machine.
On Windows, TCP/IP port assignments are stored in the C:WINDOWSSYSTEM32DRIVERSETCSERVICES file.
The original complete list of port assignments was in RFC 1700 – Assigned Numbers.
The most current official list of port assignments is maintained by the IANA (Internet Assigned Numbers Authority) at http://www.iana.org/assignments/port-numbers.


Are Hoel
On (most) Linux systems you can use netstat to see what process uses what port by adding switches: -l to show listening ports and -p to show PID/executeable. I usually add -n to avoid resolving ip and port names.