802.1x is an IEEE standard that provides the definition for the encapsulation of EAP (Extensible Authentication Protocol) and is also known as EAPOL (EAP over LAN). The standard was first defined in 2001 and later clarified in 2004 to be used with other IEEE 802 working group defined technologies such as the 802.11 wireless standard. In 2010, the protocol was further modified to support point-to-point encryption over LAN segments and service identification.
What is PPP?
PPP (Point-to-Point Protocol) and PPPoE (Point-to-Point Protocol over Ethernet) are network protocols that are used to permit communications between two or many computers, hosts, or nodes. Each of the protocols exists at the network access layer (or data link layer) with the original PPP first being defined in 1989 by the Internet Engineering Task Force (IETF). Since the original use of PPP for dial-up modem connections, it has become commonly used to provide a means for authentication between computers over a network.
What is EAP?
The Extensible Authentication Protocol, or EAP, was designed to reside inside of the PPP authentication protocol. It defines a general framework that can use a number of authentication methods. The motivation behind the development of a standardized EAP was to eliminate costly reliance on proprietary authentication solutions. Properly implemented, EAP can support the full range of methods to validate an online session to include public-key infrastructure certificates, passwords, and challenge-response tokens.
What is 802.1x?
First, 802.1x should not be confused with the 802.11x term that is commonly used to refer to all wireless specifications that have not yet reached the point of being voted an IEEE standard definition. 802.1x is an authentication protocol definition that provides for sending EAP over a wireless or wired LAN. Under the standard, EAP messages are contained in Ethernet frames and avoid the use of the PPP wrapper and saving on the overhead of the use of PPP.
How Does 802.1x Work?
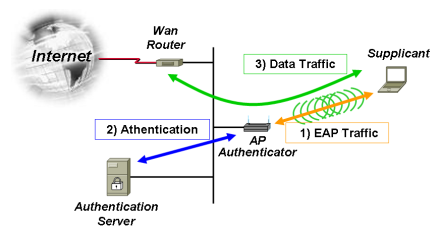
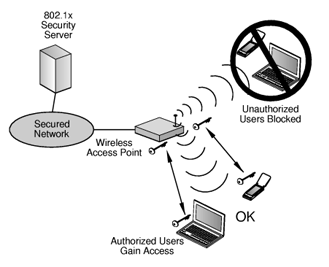
The 802.1x standard requires three participants: a supplicant, an authenticator, and an authentication server. The supplicant is typically a computer or other client device that desires to make a connection to a LAN or WAN. The term supplicant can also refer to the software application running on the computer that will provide the necessary credentials to the authenticator.
The authenticator is a network device such as a wireless access point or switch, while the required authentication server is typically a host computer that has compatible software running that supports the EAP and RADIUS protocols.
802.1X authentication involves three parties: a supplicant, an authenticator, and an authentication server. The supplicant is a client device (such as a laptop) that wishes to attach to the LAN/WLAN – though the term ‘supplicant’ is also used interchangeably to refer to the software running on the client that provides credentials to the authenticator. The authenticator is a network device, such as an Ethernet switch or wireless access point; and the authentication server is typically a host running software supporting the RADIUS and EAP protocols.
In 802.1x, the authenticator will perform a role equivalent to protecting the network. It will not permit a supplicant to access the protected side of the network until the identity of the client device has been validated and authorized access. The authenticator will provide the client’s credentials to the authentication server for verification and then permitted access to the network once approved.
IEEE Networking Standards
Although 802.1x is a more of a security-related protocol, the IEEE is also responsible for developing and releasing both security and wireless communication protocol standards for use by industry. The following is a short outline of the various networking standards released by the IEEE LAN/MAN Standards Committee since the late 1990s.
802.11 (Deprecated)
The original version of the IEEE wireless standard, 802.11, was released in 1997 and later expanded upon (or clarified) in 1999. The standard specified a data throughput of one to two megabits per second along with forward error code correction. This version of the wireless networking standard is no longer supported by industry and is deprecated.
802.11a
The 802.11a wireless networking standard was released by the IEEE in September 1999. It supported a much larger data throughput in the 20-25 Megabit/second range and works in the 5 GHz spectrum. Although 802.11a has a higher throughput than the 802.11b version released in the same timeframe, the equipment required to run the “a” standard cost more and does not have as great of range as the “b” standard.
802.11b
The IEEE 802.11b wireless networking standard was released in September 1999 and featured data rates of up to 11 Megabits per second in the 2.4 GHz band. The “b” standard was the first to see widespread use in the commercial realm and featured significantly reduced wireless networking costs when compared to the “a” standard.
802.11g
In June 2003, the 802.11g standard was released. The “g” standard operates in the 2.4 GHz frequency band and features an improved throughput over the “b” standard of 20-25 megabits per second. Other improvements with the “g” standard release include improved security options and backwards compatibility with the “b” standard.
802.11i
The 802.11i wireless security standard was first released on the 24th of June, 2004 as an amendment to the 802.11 wireless networking standard. Also known as the WPA2 security implementation, 802.11i provides an alternative to the popular, but less secure, WEP standard to encrypt wireless networks.
802.1x
802.1x was released as an IEEE security standard in 2001 and was later updated in 2004 and 2010. Designed to provide the encapsulation of EAP and EAPOL, 802.1x now provides support for service identification and point-to-point encryption over LAN segments.
802.11n
The 802.11n IEEE wireless networking standard was released in October 2009 supporting operations in the 2.4 and 5 GHz frequency bands. Supporting data throughput ranging from 54 to 600 megabits per second, the “n” standard also includes support for multiple-input, multiple-output antennas.
802.11ad
In December of 2012, the 802.11ad standard was released by the IEEE. The “ad” standard is also referred to as “WiGig” and operates in the 60 GHz frequency band. Featuring throughput in the range of 7 gigabits per second, hardware supporting the standard is expected to be sold in the marketplace in early 2014.
802.11ac
The 802.11ac wireless standard is scheduled for release in February 2014 and is still in draft form. The “ac” standard will target a one gigabit per second throughput rate and operate in the 5 GHz frequency band.
How Does the EAPOL Protocol Work?
EAPOL works in the OSI Model network layer over the data link layer. In the Ethernet II framing protocol EAPOL has an EtherType value of 0x888E. In the first version of the 802.1x standard released, there are two port entries for entry to the network. There is a “controlled port” and “uncontrolled port.” The “controlled port” is used by the PAE (Port Access Entity) to permit authorized clients to access the network or to prevent unauthorized network traffic. The “uncontrolled port” is used by the PAE to send and receive EAPOL network frames.
The revised 802.1X standard released in 2004 included the definition for equivalent port entries for the supplicant. As a result, if a supplicant implements the 2004 protocol it could prevent higher-level protocols from being used if not satisfied that the authentication was successful. When the EAP method leveraging Mutual Authentication is used, the supplicant can prevent information leakage when connected to an unauthorized network.
Typical EAP Authentication Process
The EAP process consists of the following steps: Initialization, Initiation, Negotiation, and Authentication.
Initialization: When a new supplicant is detected, the authenticator port is enabled and first set to the “unauthorized” state. Only 802.1X network traffic is allowed in this state while other IP (Internet Protocol) traffic such as UDP and TCP is dropped.
Initiation: To initiate an authentication session, the authenticator will send an EAP-Request Identity frame to a Layer 2 address located on the local network segment. The supplication opens a listening connection on the special Layer 2 address and once it receives the EAP-Request Identity frame, it will respond with an EAP-Response Identity Frame. This frame will include a supplicant identifier that on some systems can include a User ID. The network authenticator will then encapsulate the response in a RADIUS Access-Request data packet and forward to the authentication server. In this process, the supplicant can restart the authentication process or initiate another session by sending an EAPOL-Start frame to the authenticator. If this occurs, then the authenticator will send an EAP-Request Identity frame.
Negotiation:
The negotiation phase is also referred to as EAP negotiation. In this phase, the authentication server will send an encapsulated replay to the authenticator (contained in a RADIUS Access-Challenge packet). This replay will include an EAP Request that specifies the specific EAP Method to be used. The EAP request will be encapsulated by the authenticator in an EAPOL frame and then transmitted to the supplicant. From this point on, the supplicant can use the EAP Method that was requested or shift to a Negative Acknowledgement (NAK) and respond with the EAP Method that id desires to perform.
Authentication:
Once the supplicant and authentication server agree on the EAP Method, EAP responses and requests are sent between the supplicant and authentication server via the authenticator. This occurs until the authentication server responds with an EAP Success (included in a RADIUS Access-Accept packet) or EAP Failure (included in a RADIUS Access Reject packet) message. If the authentication process is successful, the authenticator will set the port to an “authorized” state and will permit regular network traffic. If not successful, the port will remain in the “unauthorized” state. When a supplicant logs off of the network, an EAPOL logoff message will be sent to the authenticator which will then change the port to an “unauthorized” state which will block all non-EAP network traffic.
How to Turn On/Off the EAP Enforcement Client
A common task that arises for Windows Server administrators is turning on or off the EAP Enforcement Client. The client can be turned on or off via the NAPCLCFG application or at the Windows command prompt.
Step 1 – Open the NAP Client Configuration console by selecting the “Start” button, clicking the “All Programs” menu option, “Accessories,” and the “Run” menu button. Then, enter “NAPCLCFG.MSC” and select the “OK” menu button.
Step 2 – Select the “Enforcement Clients” menu option.
Step 3 – Then, right click the “EAP Quarantine Enforcement Client” and select the “Enable” or “Disable” menu buttons.
Note: In order to change these configuration options, the account must be a member of the “Administrators” group on the local computer or have been delegated the applicable network authority by an administrator. If the computer is joined with a domain, the members of the “Domain Admins” group can also perform the procedure.
Steps to Turn On/Off the EAP Enforcement Client Using the Command Line
Step 1 – Select the “Start,” “All Programs,” and “Accessories” menu buttons. Then, select the “Command Prompt” menu option.
Step 2 – Enable the EAP enforcement client by entering the following command at the command prompt:
netsh nap client set enforcement ID = 79623 ADMIN = “ENABLE”
Step 3 – Disable the EAP enforcement client by entering the following command at the command prompt:
netsh nap client set enforcement ID = 79623 ADMIN = “DISABLE”


Follow Us!