The ISO, International Organization for Standardization is the Emily Post of the network protocol world. Just like Ms. Post, who wrote the book setting the standards or protocols for human social interaction, the ISO developed the OSI model as the precedent and guide for an open network protocol set. Defining the etiquette of communication models, it remains today the most popular means of comparison for protocol suites.
OSI layers are defined as top down such as:
-
The Application layer
-
The Presentation layer
-
The Session layer
-
The Transport layer
-
The Network layer
-
The Data Link layer
-
The Physical layer
Cisco Hierarchical Model
Hierarchy has many of the same benefits in network design that it does in other areas of life. When used properly, it makes networks more predictable. It helps us define at which levels of hierarchy we should perform certain functions. Likewise, you can use tools such as access lists at certain levels in hierarchical networks and avoid them at others.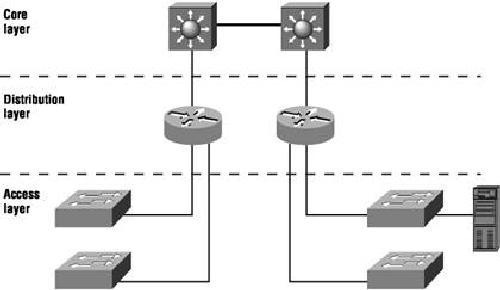
Let's face it; large networks can be extremely complicated, with multiple protocols, detailed configurations, and diverse technologies. Hierarchy helps us summarize a complex collection of details into an understandable model. Then, as specific configurations are needed, the model dictates the appropriate manner to apply them.
The Cisco hierarchical model can help you design, implement, and maintain a scalable, reliable, cost-effective hierarchical internetwork.
The following are the three layers:
-
The Core layer or Backbone
-
The Distribution layer
-
The Access layer
Each layer has specific responsibilities. However, that the three layers are logical and are not necessarily physical devices. Consider the OSI model, another logical hierarchy. The seven layers describe functions but not necessarily protocols. Sometimes a protocol maps to more than one layer of the OSI model, and sometimes multiple protocols communicate within a single layer. In the same way, when we build physical implementations of hierarchical networks, we may have many devices in a single layer, or we might have a single device performing functions at two layers. The definition of the layers is logical, not physical.
Now, let's take a closer look at each of the layers.
The Core Layer
The core layer is literally the Internet backbone. At the top of the hierarchy, the core layer is responsible for transporting large amounts of traffic both reliably and quickly. The only purpose of the network's core layer is to switch traffic as fast as possible. The traffic transported across the core is common to a majority of users. However, remember that user data is processed at the distribution layer, which forwards the requests to the core if needed.
If there is a failure in the core, every user can be affected. Therefore, fault tolerance at this layer is an issue. The core is likely to see large volumes of traffic, so speed and latency are driving concerns here. Given the function of the core, we can now consider some design specifics. Let's start with something we don't want to do.
-
Don't do anything to slow down traffic. This includes using access lists, routing between virtual local area networks, and packet filtering.
-
Don't support workgroup access here.
-
Avoid expanding the core when the internetwork grows. If performance becomes an issue in the core, give preference to upgrades over expansion.
Now, there are a few things that we want to do as we design the core. They include the following:
-
Design the core for high reliability. Consider data-link technologies that facilitate both speed and redundancy, such as FDDI, Fast Ethernet, or even ATM.
-
Design with speed in mind. The core should have very little latency.
-
Select routing protocols with lower convergence times. Fast and redundant data-link connectivity is no help if your routing tables are shot.
The Distribution Layer
The distribution layer is sometimes referred to as the workgroup layer and is the major communication point between the access layer and the core. The primary function of the distribution layer is to provide routing, filtering, and WAN access and to determine how packets can access the core, if needed.
The distribution layer must determine the fastest way that network service requests are handled; for example, how a file request is forwarded to a server. After the distribution layer determines the best path, it forwards the request to the core layer. The core layer then quickly transports the request to the correct service.
The distribution layer is the place to implement policies for the network. Here you can exercise considerable flexibility in defining network operation. There are several items that generally should be done at the distribution layer such as:
-
Implementation of tools such as access lists, of packet filtering, and of queuing
-
Implementation of security and network policies including firewalls
-
Redistribution between routing protocols, including static routing
-
Routing between VLANs and other workgroup support functions
-
Definitions of broadcast and multicast domains
Things to avoid at this layer are limited to those functions that exclusively belong to one of the other layers.
The Access Layer
The access layer controls user and workgroup access to internetwork resources. The access layer is sometimes referred to as the desktop layer. The network resources most users need will be available locally. The distribution layer handles any traffic for remote services.
The following are some of the functions to be included at the access layer:
-
Continued access control and policies
-
Creation of separate collision domains
-
Workgroup connectivity into the distribution layer through layer 2 switching
Technologies such as DDR and Ethernet switching are frequently seen in the access layer. Static routing is seen here as well. As already noted, three separate levels does not imply three separate routers. It could be fewer, or it could be more. Remember, this is a layered approach.

Follow Us!