Defining Network Infrastructure
A network can be defined as the grouping of hardware devices and software components which are necessary to connect devices within the organization, and to connect the organization to other organizations and the Internet.
- Typical hardware components utilized in a networking environment are network interface cards, computers, routers, hubs, switches, printers, and cabling and phone lines.
- Typical software components utilized in a networking environment are the network services and protocols needed to enable devices to communicate.
Only after the hardware is installed and configured, can operating systems and software be installed into the network infrastructure. The operating systems which you install on your computers are considered the main software components within the network infrastructure. This is due to the operating system containing network communication protocols that enable network communication to occur. The operating system also typically includes applications and services that implement security for network communication.
Another concept, namely network infrastructure, is also commonly used to refer to the grouping of physical hardware and logical components which are needed to provide a number of features for the network, including these common features:
- Connectivity
- Routing and switching capabilities
- Network security
- Access control
The network or network infrastructure has to exist before a number of servers needed to support applications which are needed by your users can be deployed into your networking environment:
- File and print servers
- Web and messaging servers
- Database servers
- Application servers
When you plan your network infrastructure, a number of key elements need to be clarified or determined:
- Determine which physical hardware components are needed for the network infrastructure which you want to implement.
- Determine the software components needed for the network infrastructure.
- Determine the following important factors for your hardware and software components:
- Specific location of these components
- How the components are to be installed.
- How the components are to be configured.
When you implement a network infrastructure, you need to perform a number of activities that can be broadly grouped as follows:
- Determine the hardware and software components needed.
- Purchase, assemble and install the hardware components.
- Install and configure the operating systems, applications and all other software.
The physical infrastructure of the network refers to the physical design of the network together with the hardware components. The physical design of the network is also called the network’s topology. When you plan the physical infrastructure of the network, you are usually limited in your hardware component selection by the logical infrastructure of the network
The logical infrastructure of the network is made up of all the software components required to enable connectivity between devices, and to provide network security. The network’s logical infrastructure consists of the following:
- Software products
- Networking protocols/services.
It is therefore the network’s logical infrastructure that makes it possible for computers to communicate using the routes defined in the physical network topology.
The logical components of the network topology define a number of important elements:
- Speed of the network.
- Type of switching that occurs.
- Media which will be utilized.
- Type of connections which can be formed.
Understanding the OSI Reference Model and TCP/IP Protocol Suite
The International Organization for Standardization (ISO) developed the Open Systems Interconnection (OSI) reference model for computing. The OSI model defines how hardware and software function to enable communication between computers. The OSI model is a conceptual framework which can be referenced to better comprehend how devices operate on the network. It is the most widely used guide for a networking infrastructure. When manufacturers design new products, they reference the OSI model’s concepts on the manner in which hardware and software components should function.
The OSI model defines standards for:
- How devices communicate between each other.
- The means used to inform devices when to send data and when not to transmit data.
- The methods which ensure that devices have a correct data flow rate.
- The means used to ensure that data is passed to, and received by the intended recipient.
- How physical transmission media is arranged and connected.
The OSI model is made up of seven layers which are presented as a stack. Data which is passed over the network moves through each layer. Each layer of the OSI model has its own unique functions and protocols. Different protocols operate at the different layers of the OSI model. The layer of the OSI reference model at which the protocol operates defines its function. Different protocols can operate together at different layers within a protocol stack. When protocols operate together, they are referred to as a protocol suite or protocol stack. When protocols support multiple path LAN-to-LAN communications, they are called routable protocols. The binding order determines the order in which the operating system runs the protocols.
The seven layers of the OSI reference model, and each layers’ associated function are listed here:
- Physical Layer – layer 1: The Physical layer transmits raw bit streams over a physical medium, and deals with establishing a physical connection between computers to enable communication. The physical layer is hardware specific; it deals with the actual physical connection between the computer and the network medium. The medium used is typically a copper cable that utilizes electric currents for signaling. Other media that are becoming popular are fiber-optic and wireless media. The specifications of the Physical layer include physical layout of the network, voltage changes and the timing of voltage changes, data rates, maximum transmission distances, and physical connectors to transmission mediums. The issues normally clarified at the Physical Layer include:
- Whether data is transmitted synchronously or asynchronously.
- Whether the analog or digital signaling method is used.
- Whether baseband or broadband signalling is used.
- Data-Link Layer – layer 2: The Data-link layer of the OSI model enables the movement of data over a link from one device to another, by defining the interface between the network medium and the software on the computer. The Data-link layer maintains the data link between two computers to enable communications. The functions of the Data-link layer include packet addressing, media access control, formatting of the frame used to encapsulate data, error notification on the Physical layer, and management of error messaging specific to the delivery of packets. The Data-link layer is divided into the following two sublayers:
- The Logical Link Control (LLC) sublayer provides and maintains the logical links used for communication between the devices.
- The Media Access Control (MAC) sublayer controls the transmission of packets from one network interface card (NIC) to another over a shared media channel. A NIC has a unique MAC address, or physical address. The MAC sublayer handles media access control which essentially prevents data collisions. The common media access control methods are:
- Network Layer – layer 3: The Network layer provides end-to-end communications between computers that exist on different network. One of the main functions performed at the Network layer is routing. Routing enables packets to be moved between computers which are more than one link from one another. Other functions include traffic direction to the end destination, addressing, packet switching and packet sequence control, end-to-end error detection, congestion control, and Network layer flow control and error control.
- Transport Layer – layer 4: The Transport layer deals with transporting data in a sequential manner, and with no data loss. The Transport layer divides large messages into smaller data packets so that it can be transmitted to the destination computer. It also reassembles packets into messages for it to be presented to the Network layer. Functions of the Transport layer include guaranteed data delivery, name resolution, flow control, and error detection and recovery. The common Transport protocols utilized at this layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
- Session Layer – layer 5: The Session layer enables communication sessions to be established between processes or applications running on two different computers. A process is a specific task that is associated with a particular application. Applications can simultaneously run numerous processes. The Session layer establishes, maintains and terminates communication sessions between applications. The Session layer utilizes the virtual circuits created by the Transport layer to establish communication sessions.
- Presentation Layer – layer 6: The Presentation layer is responsible for translating data between the formats which the network requires and the formats which the computer is anticipating. The presentation layer translates the formats of each computer to a common transfer format which can be interpreted by each computer. Functions include protocol conversion, data translation, data encryption and decryption, data compression, character set conversion, and interpretation of graphics commands.
- Application Layer – layer 7: The Application layer provides the interface between the network protocol and the software running on the computer. It provides the interface for e-mail, Telnet and File Transfer Protocol (FTP) applications, and files transfers. This is the location where applications interrelate with the network.
Transmission Control Protocol/Internet Protocol (TCP/IP) is a network communication protocol suite that can be utilized as the communications protocol on private networks. TCP/IP is also the default protocol utilized on the Internet. The majority of network infrastructures are based on TCP/IP.
As an engineer designing the network infrastructure, you have to provide a TCP/IP design which can provide the following:
- Connect devices in the private internal network to the Internet.
- Enable users to access TCP/IP based resources.
- Protect confidential company data.
- Provide application responses in accordance to the requirements of the organization.
The TCP/IP protocol suite is a four layer model which corresponds to seven layers of the OSI reference model:
- Network Interface layer: The Network Interface layer maps to the Physical Layer (Layer 1) and the Data-link layer (Layer 2) of the OSI reference model. The Network Interfae layer’s function is to move bits (0s and 1s) over the network medium.
- Internet layer: The Internet layer is associated with the OSI model’s Network layer. The Internet layer handles the packaging, addressing, and routing of data. The main protocols of the TCP/IP suite that operate at the Internet layer are:
- Internet Protocol (IP): IP is a connectionless, routable protocol which performs addressing and routing functions. IP places data into packets, and removes data from packets.
- Internet Control Message Protocol (ICMP): The protocol is responsible for dealing with errors associated with undeliverable IP packets, and for indicating network congestion and timeout conditions.
- Internet Group Management Protocol (IGMP): The IGMP protocol controls host membership in groups of devices, called IP multicast groups. The devices in the IP multicast groups receive traffic which is addressed to a shared multicast IP address. Unicast messages are sent to a host, while a multicast is sent to each member of an IP multicast group.
- Address Resolution Protocol (ARP): The ARP protocol maintains the associations which map IP addresses to MAC addresses. Because mappings are stored in the ARP Cache, when the same IP address needs to be mapped again to its associated MAC address, the discovery process is not performed again. Reverse Address Resolution (RARP) resolves MAC addresses to IP addresses.
- Transport layer/ Host-to-Host Transport: This layer is associated with the Transport layer of the OSI model. The main TCP/IP protocols operating at the Host to Host or Transport layer are:
- Transmission Control Protocol (TCP): TCP offers greater reliability when it comes to transporting data than what UDP, the other protocol which works at this level provides. With TCP, the application which sends the data receives acknowledgement or verification that the data was actually received. TCP is regarded as a connection-orientated protocol – a connection is established before data is transmitted. A three-part TCP handshake process is performed to establish a host to host connection. The three-part TCP handshake process establishes a reliable connection over which to exchange data.
- User Datagram Protocol (UDP): UDP does not provide reliable data transport. No acknowledgements are transmitted. While UDP is faster than TCP, it is less reliable.
- Application layer: The Application layer is associated with the Session layer, Presentation layer, and Application layer of the OSI model. Application layer protocols of the TCP/IP protocol suite functions at these layers. Application layer protocols enable applications to communicate between each other, and also provide access to the services of the lower layers.
Understanding Networking Services
Running on the physical hardware in the network infrastructure are networking services. Networking services basically extend the physical network by providing a number of key capabilities, including the following:
- Multiprotocol support, networks can run multiple protocol, including:
- Transmission ControlProtocol/Internet Protocol (TCP/IP)
- Internetwork Packet Exchange/Sequenced Packet Exchange (IPX/SPX)
- Appletalk
- Systems Network Architecture (SNA)
- Multiprotocol routing among network different network segments: The Routing and Remote Access Service (RRAS) feature of Windows 2000 and Windows Server 2003 can be used to identify networks with different topologies and secure segments of the network. The Routing and Remote Access Service can be configured for:
- LAN-to-LAN routing
- LAN-to-WAN routing
- Virtual private network (VPN) routing
- Network Address Translation (NAT) routing
- Routing features, including IP multicasting, Packet filtering, Demand-dial routing, and DHCP relay
- Support for strong network security: Internet Protocol Security (IPSec) and Virtual Private Networks (VPNs) can be used to provide a number of features. VPNs provide secure and advanced connections through a non-secure network by providing data privacy. Private data is secure in a public environment. VPN client software is assured private access in a publicly shared environment. By using analog, ISDN, DSL, cable technology, dial and mobile IP; VPNs are implemented over extensively shared infrastructures. IPSec protects, secures and authenticates data between IPSec peer devices by providing per packet data authentication. Data flows between IPSec peers are confidential and protected. IPSec supports the following:
- Unicast IP datagrams
- High-Level Data-Link Control (HDLC)
- ATM
- Point-to-Point Protocol (PPP)
- Frame Relay serial encapsulation
- Generic Routing Encapsulation (GRE)
- IP-in-IP (IPinIP)
- Encapsulation Layer 3 tunneling protocols.
- Enable connectivity between the private internal network and Internet applications: Networking services such as the RRAS service and Network Address Translation (NAT) service enable users on the private internal network to connect to the Internet, while at the same time securing resources located on the private network.
- NAT translates IP addresses and associated TCP/UDP port numbers on the private network to public IP addresses which can be routed on the Internet. Through NAT, host computers are able to share a single publicly registered IP address to access the Internet. NAT also offers a number of security features which can be used to secure the resources on your private network.
- RRAS IP packet filters can be used to restrict incoming or outgoing IP address ranges based on information in the IP header. You can configure and combine multiple filters to control network traffic. You can also map external public IP addresses and ports to private IP addresses and ports so that internal private resources can be accessed by Internet users. You use a special port to map specific Internet users to resources within the private network.
- The Internet Connection Sharing (ICS) service is basically a simplified implementation of a Network Address Translation (NAT) server. You can use ICS to connect the entire network to the Internet. This is due to the ICS service providing a translated connection – all computers can access resources on the Internet. Implementing ICS is though only recommended for those exceptionally small networks.
- Microsoft Proxy Server can also be used to provide connectivity between the private internal network, and Internet applications.
- Enable users to remotely access the private network. The service that enables this capability is the Routing and Remote Access Service (RRAS). The different types of remote access are:
- Dial-in remote access: Dial-in remote access uses modems and servers running the Routing and Remote Access (RRAS) service. To enable communication, dial-in access utilizes the Point-to-Point (PPP) protocol.
- VPN remote access: A VPN provides secure and advanced connections through a non-secure network. With VPN access, encryption is used to create the VPN tunnel between the remote client and the corporate network. To secure VPN access, Windows Server 2003 provides strong levels of encryption.
- Wireless remote access: Wireless networks are defined by the IEEE 802.11 specification. With wireless networks, wireless users connect to the network through connecting to a wireless access point (WAP). To secure wireless networks and wireless connections, administrators can require all wireless communications to be authenticated and encrypted. When planning wireless remote access, planning security for wireless networks should be a high priority factor.
- Name resolution capabilities: The Domain Name System (DNS) service or Windows Internet Name Service (WINS) service can be used to resolve host names to IP addresses. Name resolution has to occur whenever the host name is used to connect to a computer and not the IP addresses. Name resolution has to occur so that the IP address can be resolved to the hardware address for TCP/IP based communication to occur.
- The DNS service resolves host names and fully qualified domain names (FQDNs) to IP addresses in TCP/IP based networks. The DNS server manages a database of host name to IP address mappings. This is the primary method used for name resolution in Windows Server 2003.
- WINS is an enhanced NetBIOS name server (NBNS) which was designed by Microsoft to resolve NetBIOS computer names to IP addresses, and at the same time eliminate the usage of broadcasts for name resolution. WINS can resolve NetBIOS names for local hosts and remote hosts.
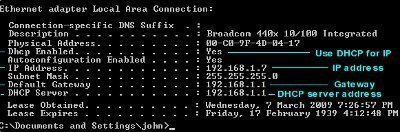
- Automatic configuration of IP addressing and other IP parameters: The Dynamic Host Configuration Protocol (DHCP) service simplifies the administration of IP addressing in TCP/IP based networks. One of the primary tasks of the protocol is to automatically assign IP addresses to DHCP clients. A server running the DHCP service is called a DHCP server. The DHCP protocol automates the configuration of TCP/IP clients because IP addressing occurs through the system. IP addresses that are assigned via a DHCP server are regarded as dynamically assigned IP addresses. The DHCP server assigns IP addresses from a predetermined IP address range(s). The functions of the DHCP server running the DHCP service are listed here:
- Dynamically assign IP addresses to DHCP clients.
- Assign the following TCP/IP configuration information to DHCP clients:
- Subnet mask information
- Default gateway IP addresses
- Domain Name System (DNS) IP addresses.
- Windows Internet Naming Service (WINS) IP addresses.
There are a number of tools and features included with Windows 2000 and Windows Server 2003 that can be used to manage and monitor the networking services which you deploy within your networking infrastructure.
Network Infrastructure Planning Overview
Planning network infrastructure is a complex task that needs to be performed so that the network infrastructure needed by the organization can be designed and created. Proper planning is crucial to ensure a highly available network and high performance network that result in reduced costs and enhances business procedures for the organization.
To properly plan your network infrastructure, you have to be knowledgeable on a number of factors, including the following:
- Requirements of the organization.
- Requirements of users.
- Existing networking technologies.
- Necessary hardware and software components.
- Networking services which should be installed on the user’s computers so that they can perform their necessary tasks.
A typical network infrastructure planning strategy should include the following:
- Determine the requirements of the organization and its users, and then document these requirements.
- Define a performance baseline for all existing hardware devices.
- Define a baseline for network utilization as well.
- Identify the capacity for the physical network installation. This should encompass the following:
- Server hardware, client hardware.
- Allocation of network bandwidth for the necessary networking services and applications.
- Allocation of Internet bandwidth
- Determine which network protocol will be used.
- Determine which IP addressing method you will use.
- Determine which technologies, such as operating systems and routing protocols are needed to cater for the organization’s needs as well as for possible future expansions.
- Determine the security mechanisms which will be implemented to secure the network and network communication.
After planning, the following step would be to implement the technologies which you have identified. Implementation of the network infrastructure involves the following tasks:
- Installing the operating systems.
- Installing the necessary protocols and software components.
- Deploying DNS or WINS name resolution.
- Designing the DNS namespace.
- Assigning IP addresses and subnet masks to computers.
- Deploying the necessary applications.
- Implementing the required security mechanisms.
- Defining and implementing IPSec policies.
- Determining the network infrastructure maintenance strategy which you will employ once the network infrastructure is implemented. Network infrastructure maintenance consists of the following activities:
- Upgrading operating systems.
- Upgrading applications.
- Monitoring network performance, processes and usage.
- Troubleshooting networking issues.
Windows Server 2003 includes a number of features, and user and computer management tools that can be utilized to plan the network configuration:
- The Resultant Set of Policy (RSoP) MMC snap-in can be used to determine the effects of applying changes to Group Policy Objects (GPOs) in Windows 2000 and Windows Server 2003 Active Directory environments before applying the changes.
- The Group Policy Management Console (GPMC) can be used if you want to view configuration information on the existing GPO settings in Windows 2000 and Windows Server 2003 Active Directory environments.
Determining Network Layer and Transport Layer Protocols
Windows Server 2003 supports the following network layer and transport layer protocol combinations:
- Transmission Control Protocol/Internet Protocol (TCP/IP): TCP/IP is a grouping of protocols which provides a collection of networking services. TCP/IP is the main protocol which Windows Server 2003 utilizes for its network services. The main protocols in the TCP/IP suite are Transmission Control Protocol (TCP) that operates at the Transport layer, and Internet Protocol (IP) that operates at the Network layer. When communication takes place through TCP/IP, IP is used at the Network layer, and either TCP or UDP is used at the Transport layer. With TCP/IP, the TCP component of the protocol suite utilizes port numbers to forward messages to the correct application process. Port numbers are assigned by the Internet Assigned Numbers Authority (IANA), and they identify the process to which a particular packet is connected to. Port numbers are found in the packet header.
The main advantages of using TCP/IP are summarized below:
- Can be used to establish connections between different types of computers and servers.
- Includes support for a number of routing protocols.
- Enables internetworking between organizations.
- Includes support for name and address resolution services, including Domain Name Service (DNS), Dynamic Host Configuration Protocol (DHCP), and Windows Internet Name Service (WINS).
- Includes support for a number of different Internet standard protocols for Web browsing, file and print services, and transporting mail.
The disadvantages of TCP/IP are summarized below:
- IPX is faster than TCP/IP.
- TCP/IP is intricate to set up and manage.
- The overhead of TCP/IP is higher than that of IPX.
- Internetwork Packet Exchange (IPX): The Microsoft implementation of Novell’s IPX/SPX protocol stack is NWLink IPX/SPX. NWLink IPX/SPX is used in Novell NetWare, and is basically IPX for Windows. Windows Server 2003 includes NWLink IPX/SPX support to enable Windows Server 2003 to communicate with legacy Novell NetWare servers and clients. NWLink IPX/SPX could become problematic in large networks because it does not have a central IPX addressing scheme which prevents networks from utilizing the same address numbers.
The main advantages of NWLink IPX/SPX are summarized below:- NWLink IPX/SPX is simple to implement and manage.
- Connecting to is NetWare servers and clients is a simple process.
- NWLink IPX/SPX is routable
The disadvantages of NWLink IPX/SPX are summarized below:
- Windows Server 2003 only includes limited support for NWLink IPX/SPX.
- Exchanging data between different organizations via NWLink IPX/SPX is an intricate process.
- NWLink IPX/SPX does not support standard network management protocols.
- NetBIOS Extended User Interface (NetBEUI): NetBIOS naming is supported in Windows Server 2003. Windows Server 2003 does not though support the NetBEUI protocol. NetBEUI is a single protocol that was initially used in Windows NT 3.1 and Windows for Workgroups operating systems. The protocol provides basic file sharing services for Windows computers, and is designed for small networks. NetBEUI does not perform well on large networks. The protocol can also not support internetwork traffic because it cannot route traffic between networks. NetBEUI cannot address traffic to a computer on a different network
TCP/IP Design Requirements
Before deciding to use a TCP/IP based network design, you first have to determine whether you actually need to utilize TCP/IP. Whether a TCP/IP based network design is required or not is dictated by the networking services and applications required within your network infrastructure:
- The Active Directory directory service uses the Lightweight Directory Access Protocol (LDAP) and Domain Name System (DNS). These protocols are dependent on TCP/IP.
- Domain Name System (DNS) is the primary name resolution method used in Windows Server 2003, and is dependent on TCP/IP being installed.
- Web servers use the File Transfer Protocol (FTP) protocol and HTTP protocol, which are each reliant on TCP/IP.
- As mentioned earlier, the default protocol on the Internet is TCP/IP. In fact, all Internet protocols are based on TCP/IP. If you are planning to enable internet connectivity, TCP/IP is a requirement.
- Both Line Printer Daemon (LPD) and PrinterRemote (LPR) printers need TCP/IP to be installed.
- To enable interoperability between Unix and other operating systems, TCP/IP is used as the common transport protocol.
In order to implement a TCP/IP network infrastructure, you have to gather a number of design requirements, including the following:
- The existing TCP/IP network’s characteristics, if applicable, should include:
- The number of network segments which currently exist.
- The IP address range assigned to the organization.
- The routing protocols being utilized.
- The attributes of the data which is to be transmitted over the network segments:
- The quantity of data transmitted over each network segment.
- The confidentiality requirements of the data.
- The amount of tie which users need to access the network.
- The desired response times for any applications that access resources in the network.
- Possible future network expansion expectations.
There are a number of additional factors which need to be determined before you can create a routing solution for your network:
- The IP addressing scheme which will be utilized.
- The IP subnet masks which will be utilized.
- The Variable Length Subnet Masks (VLSMs) which will be utilized.
- The Classless Interdomain Routing utilization.
- The standards for creating TCP/IP filters
- The authentication methods for protecting access to the private network.
- The encryption algorithms for ensuring data confidentiality.
Determining the IP Addressing Scheme
The IP addressing scheme which you use can be based on:
- Public IP addresses: Here, the IP addressing scheme consists of only public IP addresses.
- Private IP addresses: Here, the IP addressing scheme consists of private IP addresses and a small number of public IP addresses needed to enable Internet connectivity.
If you are only using a public IP addressing scheme in your network design, then you need to perform the following activities:
- Purchase a range of public IP addresses from an ISP that is approved by the Internet Corporation for Assigned Names and Numbers (ICANN).
- The IP address range should have sufficient IP addresses for all interfaces in your network infrastructure design. Devices that connect to the private network need an IP address, and so too does VPN connections.
- You need to be certain that network address translation (NAT) is not required.
- You need to implement firewalls and router packet filters to secure the resources within your private network from Internet users.
If you are implementing a private IP addressing scheme, then the network design would consist of the following:
- Private IP addresses would be assigned to all devices in the private internal network.
- Public IP addresses would be assigned to all devices connecting to the public network.
The selection of the IP address range needed for the organization should be based on the following factors:
- Maximum number of IP devices on each subnet
- Maximum number of network subnets needed in the network design.
If you are using a private IP addressing scheme in your network design, consider the following important points:
- For those IP devices that connect the company network to public networks such as the Internet, you need to obtain a range of public IP addresses from the ISP for these devices.
- You should only assign public IP addresses to those devices that communicate directly with the Internet. This is mainly due to you paying for each IP address obtained. Devices which directly connect to the Internet are your network address translation (NAT) servers, Web servers, VPN remote access servers, routers, firewall devices, and Internet application servers.
- The private IP address range which you choose should have sufficient addresses to support the number of network subnets in your design, and the number of devices or hosts on each particular network subnet.
- You must cater for a network address translation (NAT) implementation. NAT translates IP addresses and associated TCP/UDP port numbers on the private network to public IP addresses which can be routed on the Internet. Networks that do not require an implementation of a firewall solution or a proxy server solution can use NAT to provide basic Internet connectivity. Through NAT, host computers are able to share a single publicly registered IP address to access the Internet.
IP version 6 (IPv6) was designed to deal with the current shortage of IP addresses with IP version 4 (IPv4). IP version 6 also includes some modifications to TCP/IP.
The primary differences between IPv6 and IPv4 are listed here
- Source and destination addresses: IPv4: 128 bits in length; IPv6: 32 bits in length
- IPSec support: IPv4: Optional; IPv6: Required.
- Configuration of IP addresses: IPv4: Manually or via DHCP; IPv6: Via Address Autoconfiguration – DHCP is no longer required, nor is manual configuration.
- Packet flow identification for QoS handling in the header: IPv4: No identification of packet flow; IPv6: Packet flow identification for QoS handling exists via the Flow Label field.
- Broadcast addresses: IPv4: Broadcast addresses are used to transmit traffic to all nodes on a specific subnet; IPv6: Broadcast addresses are replaced by a link-local scope all-nodes multicast address.
- Fragmentation: IPv4: Performed by the sending host and at the routers; IPv6: Performed by the sending host.
- Reassembly: IPv4: Has to be able to reassemble a 576-byte packet; IPv6: Has to be able to reassemble a 1,500-byte packet.
- ARP Request frames: IPv4: Used by ARP to resolve an IPv4 address to a link-layer address; IPv6: Replaced with Neighbor Solicitation messages.
- ICMP Router Discovery: IPv4: Used to determine the IPv4 address of the optimal default gateway; IPv6: Replaced with ICMPv6 Router Solicitation and Router Advertisement messages.
- Internet Group Management Protocol (IGMP): IPv4: Used to manage local subnet group membership; IPv6: Replaced with Multicast Listener Discovery (MLD) messages.
- Header checksum: IPv4: Included; IPv6: Excluded
The advantages of IPv6 are listed below:
- Large address space: Because of the larger number of available addresses, it is no longer necessary to use utilize Network Address Translator (NAT) to map a public IP address to multiple private IP addresses.
- A new header format which offers less overhead: The new header format of IPv6 is designed to minimize header overhead. All optional fields which are needed for routing are moved to extension headers. These extension headers are located after the IPv6 header. The IPv6 header format is also streamlined so that it is more efficiently processed at intermediate routers. The number of bits in IPv6 addresses is four times larger than IPv4 addresses.
- An efficient hierarchical addressing and routing infrastructure: The IPv6 global addresses are designed to create an efficient routing infrastructure.
- Built in support for security – IPSec: A requirement of IPv6 is support for IPSec. IPSec contains the following components that provide security:
- Authentication header (AH): The AH provides data authentication, data integrity and replay protection for the IPv6 packet. The only fields in the IPv6 packet that are excluded are those fields that change when the packet moves over the network.
- Encapsulating Security Payload (ESP) header: The ESP header provides data authentication, data confidentiality, data integrity, and replay protection for ESP encapsulated payload
- Internet Key Exchange (IKE) protocol: The IKE protocol is used to negotiate IPSec security settings.
- Support for Stateless and stateful address configuration: IPv6 can support a stateful address configuration and a stateless address configuration. With IPv4, hosts configured to use DHCP have to wait a minute before they can configure their own IPv4 addresses. Stateless address configuration however enables a host on a link to automatically configure its own IPv6 address for the link. These addresses are called link-local addresses. A link-local address is configured automatically, even when no router exists. This allows communication between neighboring nodes on the same link to occur immediately.
- Support for Quality of service (QoS) header fields: There are new fields in the IPv6 header that specify the way traffic is identified and handled.
- Traffic Class field: This field defines traffic that must be prioritized.
- Flow Label field: This field enables the router to identify packets, and also handle packets that are part of the identical flow in a special way.
- Unlimited extension headers: You can add extension headers after the IPv6 header if you want to extend IPv6 for any new features.
- The Neighbor Discovery (ND) protocol for managing nodes on the same link: Neighbor Discovery is a series of Internet Control Message Protocol for IPv6 (ICMPv6) messages that are used in IPv6 environments to identify the relationships between neighboring nodes. ND enables hosts to discover routes on the same segment, addresses and address prefixes. Address Resolution Protocol (ARP), ICMPv4 Router Discovery and ICMPv4 Redirect messages are replaced with the more efficient multicast and unicast Neighbor Discovery messages.
If you want an IP address to provide all services to the network, then each particular service must have a unique TCP port or UDP port from that specific IP address. There are a number of well-known ports which are used by the different services running on your computers.
The main port numbers used by protocols/services running on your computers are listed here:
- Port 20; for File Transfer Protocol (FTP) data
- Port 21; for File Transfer Protocol (FTP) control
- Port 23; for Telnet.
- Port 25; for Simple Mail Transfer Protocol (SMTP)
- Port 37; for Time Protocol.
- Port 49; for Terminal Access Controller Access Control System (TACACS) and TACACS+
- Port 53; for DNS.
- Port 67; for BOOTP server.
- Port 68; for BOOTP client.
- Port 69; for TFTP.
- Port 70; for Gopher.
- Port 79; for Finger.
- Port 80; for Hypertext Transfer Protocol (HTTP)
- Port 88; for Kerberos
- Port 109; for Post Office Protocol version 2 (POP2)
- Port 110; for Post Office Protocol version 3 (POP3)
- Port 115; for Simple File Transfer Protocol (SFTP)
- Port 119; for Network News Transfer Protocol (NNTP)
- Port 123; for Network Time Protocol (NTP)
- Port 137; for NetBIOS Name Service
- Port 138; for NetBIOS Datagram Service
- Port 139; for NetBIOS Session Service
- Port 143; for Internet Message Access Protocol (IMAP)
- Port 153; for Simple Gateway Monitoring Protocol (SGMP)
- Port 161; for SNMP
- Port 161; for SNMP traps
- Port 179; for BGP
- Port 389; for Lightweight Directory Access Protocol (LDAP) and Connectionless Lightweight X.500 Directory Access Protocol (CLDAP)
- Port 443; for Secure HTTP (HTTPS)
- Port 500; for Internet Key Exchange (IKE)
- Port 546; for DHCPv6 client
- Port 547; for DHCPv6 server
- Port 631; for Internet Printing Protocol (IPP)
Determining Locations of Network Components
When planning locations for your hardware and software components, the factors that you need to consider are primarily determined by how your users need to access your devices to carry out their daily tasks.
When determining locations for cables, a few important factors to consider are listed here:
- To maintain the network infrastructure, you need to be knowledgeable on where cables are located.
li>You also need to know how cables are arranged when needing to both maintain and troubleshoot network infrastructure issues. - When determining locations for cables and the routing strategy of your cables, you need know what the locations are of any obstacles which could affect the performance of your cables. These obstacles should be bypassed.
- When routing cables, there are a number of components which cables have to either pass around or through, that have to be determined:
- Air conditioning ducts.
- Firewalls
- Plenums
- You would need to determine the manner in which the cables should be installed.
- In cases where the cables have to run down into the center of the room from the ceiling, it important to determine the precise location of the utility pole that will hold the cables.
- You need to determine the location of each cable terminus.
- You should cater for additional cable runs for any future network expansion plans.
When determining locations for connectivity devices, a few important factors to consider are listed here:
- You need to determine the locations of hubs and patch panels.
- The network’s size and the installation site determines the following:
- Locations of hubs and patch panels.
- Number of hubs and patch panels needed.
- You should always include ceiling heights in your planning – remember that cable runs are typically longer than what they seem because they run around obstacles.
- The size of the network and the protocols which you plan to utilize determines how connectivity is established. For instance, hubs and switches can be used to connect building floors. Routers can be used to create an internetwork.
When determining locations for servers, a few important factors to consider are listed here:
- Servers need to be physically secured and protected from power strikes and interruptions.
- With internetworks, the locations of your users that need to access servers is a determining factor for server placement.
- If you are planning to use departmental servers for your network, place these servers in locked closets.
- A better option to using a departmental server strategy is to place all servers in a central data center. It is easier to physically secure servers when they reside in a single data center.
- For servers that need to be accessed by all users within the organization, you need to place these servers where they can directly be connected to the backbone network.
When determining locations for workstations, a few important factors to consider are listed here:
- Before placing any workstation, you need to determine which computer type is needed.
- You also need to determine how workstations should be placed relative to the actual desk.
When determining locations for printers and other shared components, a few important factors to consider are listed here:
- Printers should be placed where users can easily access them.
- Be careful when placing printers that release gases when they operate as it can cause a discomfort to users.
- When determining the location of printers, include factors such as maintenance access to the printer, and the locations of the printer’s supplies (toner, paper).




Asio Rosebell
thank you this was very helpfull