Understanding the Different Server Roles
The server roles that exist in a networking environment are standalone servers, member servers and domain controllers. A standalone server is a computer that is not member of a domain, and can be a computer running Windows NT 4, Windows 2000 or Windows Server 2003. A test server is a good example of a standalone server. Standalone servers do not use Active Directory for authentication and access control because they are not included in the Active Directory domain. These servers use the local Security Accounts Manager (SAM) database on the local machine for access control.
A member server is a machine that holds a replica of the Active Directory data store, and is a member of the domain, but it does not perform any domain management functions. Because a member server operates as a member of the domain, it has a computer account within the domain. Users and computers can be authenticated and managed via the domain. Member servers are your print servers, file servers, application servers, e-mail servers, Terminal Services serves, Web servers, DNS servers, WINS servers, DHCP servers, NAT servers and Remote Access servers.
In Windows NT, you had to choose the role of the servers during the installation of the operating system. The server could be configured as a Primary Domain Controller (PDC), a Backup Domain Controller (BDC), or a member server. Changes to the security database could only be made from the server configured as a PDC. You could only promote a BDC to a PDC. If you wanted to change the role of a server from a member server, to a domain controller, you had to completely reinstall Windows NT. With Windows 2000, came the concept of promoting member servers to domain controllers and demoting domain controllers back to the member server role. Thus, all machines in Windows 2000 and Windows Server 2003 have either the standalone server role or member server role when they start out.
A domain controller is a computer running Windows 2000 or Windows Server 2003 that hosts a replica of the Active Directory data store, and is a member of the Active Directory domain. A domain controller performs various Active Directory operations within the domain such as granting access to, or denying access to network resources hosted in the domain.
The Role of Domain Controllers
A domain controller performs the following operations within an Active Directory domain:
A domain controller holds a replica of the Active Directory directory for the domain to which it belongs. It is also responsible for managing that directory.
-
The domain controller is responsible for replicating all changes made to their Active Directory replica to the remainder of the domain controllers within the domain. The default replication setting is that domain controllers in a site replicate changes made to its replica of Active Directory to all domain controllers within the domain each 15 minutes. You can control the amount of replication traffic that is generated within your Active Directory environment by specifying how often replication should occur.
-
Domain controllers also manage access to network resources in the domain. They locate Active Directory objects, authenticate access to these objects, validate user logon attempts, and authenticate user passwords. User account changes such as an account being disabled is immediately replicated by the particular domain controller to all domain controllers within the domain.
-
Domain controllers track user account information through Security Identifiers (SIDs). a user attempts to log on to the system, a request to authenticate the user is sent to each domain controller within the domain. The user is authenticated via Kerberos security after a domain controller is located and a secure connection is established. Authentication is based on the user providing a username and password that correspond to those in the Active Directory database. The session information, or access token of the account is stored in memory. This includes rights and group membership details. When the user attempts to access network resources, the access token and the permissions of the resource are compared to ascertain what access is permitted to the network resource.
-
Multiple domain controllers provide fault tolerance in your Active Directory environment. In the Windows NT domain model, no changes could be made to the domain database when the primary domain controller was unavailable. With Active Directory, because domain controllers function as peers to one another, changes can be made to the Active Directory database from any domain controller in the domain. When a domain controller is unavailable, the remainder of the domain controllers continue to provide access to network resources.
-
Domain controllers also integrate with network services such as DNS, DHCP, Kerberos security, and Remote Access. This in turn facilitates centralized management and security.
Considerations for Multiple Domain Controllers
The number of domain controllers which are needed within your domain are determined by the following factors:
-
The number of users in the domain
-
The number of computers in the domain
-
The application requirements in the domain
-
The level of fault tolerance required for the domain – at least two domain controllers should exist in the domain.
-
The following domain functions and roles affect performance, and therefore influence the number of domain controllers that should be deployed in the domain:
-
Active Directory replication affects Active Directory performance. Keeping domain controllers synchronized typically generates replication traffic.
-
Active Directory performance is also affected when computer accounts authenticate to the domain.
-
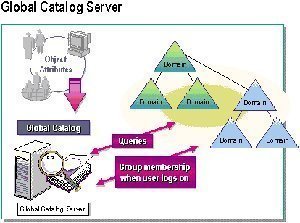
Global Catalog (GC) operations that are necessary when multiple domains exist in a forest also affect domain performance, and thereby influence the number of domain controllers that should be deployed in the domain.
-
A domain controller can host network services such as DNS, DHCP, or WINS services; and can be a file server or print server as well.
-
The PDC Emulator: The initial domain controller that is installed is assigned the PDC Emulator Flexible Single Master Operations (FSMO) role. The FSMO interacts with Windows NT 4 backup domain controllers, and receives all account lockout and new password information for the domain.
-
Other FSMOs also affect the performance of the domain controller.
-
User authentication and access control to network resources also affect performance.
-
How to create the first domain controller
A domain controller can be installed through the use of the Active Directory Installation Wizard. Through wizard, you can configure Active Directory on a member server, thereby making it a domain controller. You can also demote the domain controller to being a member server at a later stage, when it no longer needs to perform Active Directory functions. Before Active Directory can be installed, be sure to verify that DNS is installed and working.
Use the steps below to create a domain controller
-
Log on to the member server that you want to configure as a domain controller
-
Click Start, click Run, and enter dcpromo in the Run dialog box. Click OK.
-
This action starts the Active Directory Installation Wizard.
-
On the initial Welcome page of the wizard, click next.
-
On the Operating System Compatibility page, click Next.
-
On the Domain Controller Type page, you are prompted to choose one of the options listed below. Click Next after you have selected the appropriate option.
-
Domain controller for a new domain: If you choose this option, the server becomes the first domain controller in a new domain. The option is typically chosen for each new domain being created.
-
Additional domain controller for an existing domain: If you choose this option, the server that you are promoting to be domain controller has to be able to locate another domain controller through DNS. This option is typically used to create additional domain controllers for an existing domain, and to create domain controllers for each site within your Active Directory environment.
-
-
The options available on the Create New Domain Page are listed below. Once you have made the appropriate selection, click Next
-
Domain in a new forest: If this is the first domain controller being created, you would select this option. The domain, domain tree, and forest would are all created when you create the first domain controller.
-
Child domain in an existing domain tree: This option is selected if you are adding another domain (child domain) to an existing domain (parent domain).
-
Domain tree in an existing forest: This option is chosen if you want to add another domain tree to an existing forest.
-
-
On the New Domain Name page, you have to enter the fully qualified domain name (FQDN) of the new domain. Click Next
-
On the NetBIOS Domain Name page, you have to verify whether the default NetBIOS domain name should be used. You can accept the default name by clicking Next.
-
On the Database and Log Folders page, you have to specify a location for the Active Directory database, and specify a location for the Active Directory log files. The locations that you specify should preferably exist on an NTFS volume. Click Next.
-
On the Shared System Volume page, you need to specify the location of the SYSVOL folder. This folder has to be located on a NTFS volume. Click Next.
-
On the DNS Registration Diagnostics page, you can choose one of the following options:
-
I have corrected the problem. Perform the DNS diagnostics test again: This option is usually selected after you have corrected a previous DNS server problem, and you are attempting to run the Active Directory Installation Wizard again.
-
Install and configure the DNS server on this computer to use this DNS server as its preferred DNS server: This is the default setting on the DNS Registration Diagnostics page. If selected, the Active Directory Installation Wizard creates and configures the DNS server on the machine.
-
I will correct the problem later by configuring DNS manually: It is generally recommended to not select this option.
-
-
On the Permissions page, you have to choose the default permissions for user and group objects. The options available are:
-
Permissions compatible with pre-Windows 2000 server operating systems
-
Permissions Compatible only with Windows 2000 or Windows Server 2003
-
-
On the Directory Services Restore Mode Administrator Password page, you have to enter the appropriate password in the two password text boxes.
-
The Summary page lists all the configuration settings that you have specified while navigating through the various pages of the Active Directory Installation Wizard. Once you have verified that the correct settings have been specified, click Next
-
At this stage, the Active Directory Installation Wizard installs Active Directory.
-
On the Completing the Active Directory Installation Wizard page, click Finish. If this is the first domain controller, it is placed in the Default-First-Site-Name default site.
How to create additional domain controllers
After you have created the first domain controller for a domain, you can create additional domain controllers for the domain. This process is typically known as promoting a member server or standalone server to an additional domain controller role. To create an additional domain controller, you would need an existing domain controller, and a standalone server or member server that is connected on the same network, and using the same DNS server.
Use the steps below to create additional domain controllers for a domain:
-
Log on to the member server or standalone server that you want to promote to an additional domain controller.
-
Click Start, click Run, and enter dcpromo in the Run dialog box. Click OK to start the Active Directory Installation Wizard.
-
Click Next on the initial Welcome page of the wizard and on the Operating System Compatibility page.
-
On the Domain Controller Type page, select the Additional domain controller for an existing domain option. Click Next
-
On the Network Credentials page, enter the user name, password and domain for the Administrator account being used to install Active Directory on the server. Click Next
-
On the Additional Domain Controller page, enter the FQDN domain name of the domain to which this particular server is to be an additional domain controller for. Click Next
-
On the Database and Log Folders page, you have to specify a location for the Active Directory database, and specify a location for the Active Directory log files. Click Next.
-
On the Shared System Volume page, you need to specify the location of the SYSVOL folder. This folder has to be located on a NTFS volume. Click Next.
-
On the Directory Services Restore Mode Administrator Password page you have to enter the appropriate password in the password text boxes.
-
The Summary page lists all the configuration settings that you have specified while navigating through the various pages of the Active Directory Installation Wizard. Once you have verified that the correct settings have been specified, click Next
-
On the Completing the Active Directory Installation Wizard page, click Finish.
Upgrading Domain Controllers
You can upgrade existing domains to Windows Server 2003 by individually upgrading your domain controllers. You can upgrade an existing domain through one of the following methods:
-
In-place upgrade: In this case, Windows Server 2003 is installed on your existing domain controllers. What this means is that the existing domain structure is moved into Windows Server 2003 Active Directory with no need to create new SIDs or trust relationships. Users also keep their passwords. In-place upgrades generally work well if you are moving from Windows 2000 to Windows Server 2003 Active Directory. It is generally recommended to not perform an in-place upgrade in the following cases:
-
You cannot use an in-place upgrade to join a Windows NT 4 domain to an Active Directory domain.
-
If your purpose is to place a Windows NT 4 primary domain controller in an existing Active Directory domain as a domain controller, you should not attempt to perform an in-place upgrade. The in-place upgrade will create a new domain when upgrading the Windows NT 4 primary domain controller (PDC).
-
-
Migration: With migration, you basically need to create a new instance of Active Directory on a computer, and then migrate your users, computers and groups into it from the existing domain. A set of migration wizards included in the Active Directory Migration Tool is provided by Microsoft to assist with migrations.
A few advantages associated with a migration are summarized below:
-
Because accounts are copied, you can use the old domain name if you need to.
-
A migration allows you to closely examine the existing domain structure. This in turn would enable you to expand or join the domains. You can also try to refrain from moving existing problems in the security database to the new installation of Active Directory.
-
Because migration is a slow process, you can individually migrate departments within your organization.
A few disadvantages associated with a migration are:
-
New hardware is required for a migration. With a migration, Active Directory is installed on a new computer.
-
Migrations usually involve a vast quantity of planning and work.
-
The NetBIOS name that was used in the existing domain cannot be used in the new Active Directory domain.
-
The Active Directory Migration Tool (ADMT) is best suited to handle migrations for small to medium sized domains. For large enterprise domains, you would need to purchase migration tools.
The steps typically required to perform an in-place upgrade of a Windows Server NT 4 domain to a Windows Server 2003 forest is listed below:
-
Create a placeholder domain to be the root domain of the forest to simplify the installation process. You would then create the first domain controller in the placeholder domain. You can raise the domain functional level to Windows Server 2003 when the domain controller is up and running.
-
Upgrade the primary domain controller and the backup domain controllers of the first account domain. To do this, use the Windows Server 2003 CD to start the upgrade wizard for upgrading the operating system. The Active Directory Installation Wizard automatically starts after the operating system is upgraded. You would need to select the Domain In An Existing Tree option to join the forest at the previously created placeholder domain.
-
Raise the domain functional level to Windows Server 2003 functional level for the first account domain. You would need to use the Active Directory Domains and Trusts console to raise the functional level of the domain.
-
Upgrade the primary domain controller and the backup domain controllers of the resource domains beneath the first account domain.
-
Raise the domain functional level to Windows Server 2003 functional level for the resource domains through the Active Directory Domains and Trusts console.
-
Upgrade the primary domain controller and the backup domain controllers of all other account domains.
-
Raise the domain functional level to Windows Server 2003 functional level for these domains. Use Active Directory Domains and Trusts to perform this task.
-
Raise the forest functional level to Windows Server 2003 forest functional level. Use Active Directory Domains and Trusts to perform this task.
The steps typically required to perform an in-place upgrade of a Windows 2000 forest to Windows Server 2003 noted below:
-
Upgrade the Active Directory schema. Before you can update the schema, each domain controller must be running Windows 2000 with Service Pack 2 or above. You can use the ADPREP utility located on the Windows Server 2003 CD-ROM to upgrade the schema.
-
Use adprep /forestprep to perform the schema upgrade.
-
Use adprep /domainprep to apply new attributes to the Domain object, and to add the container used for tracking domain updates.
-
-
Upgrade the existing domain controllers in the root domains.
-
Raise the domain functional level to Windows Server 2003 domain functional level.
-
Upgrade the existing domain controllers in the child domains.
-
Raise the domain functional level to Windows Server 2003 domain functional level.
-
Raise the functional level of the forest to Windows Server 2003 forest functional level.
-
Create the forest trust relationships.
Backing up Domain Controllers
Before looking at how to backup the domain controllers within your Active Directory environment, it is important to note that you can also create domain controllers by using a backup of Active Directory. This basically involves performing a restore to the server that you want to promote to a domain controller. You have to be a member of the Administrators group or the Backup Operators group to perform the backup process.
A domain controller contains system state data that also includes Active Directory and the SYSVOL directory. System state data consists of the Registry, system bot files, COM+ Class Registration database, Certificate Services database, and files under Windows File Protection. Backing up system state data backs up all system state data associated with the local computer. A domain controller can also contain applications or files that are specific to that particular domain controller. These have to be included when you back up the domain controller. You cannot back up system state data on a remote computer. What this means is that you have to be logged on to the computer locally.
How to perform a domain controller backup
-
Log on to the domain
-
Click Start, All Programs, Accessories, System Tools, and then click Backup.
-
When the Welcome To The Backup Or Restore Wizard page opens, click Next.
-
In the Backup Or Restore page, choose the Backup Files And Settings option. Click Next.
-
When the What To Back Up page opens, choose the Let Me Choose What To Back Up option. Click Next.
-
In the Items To Back Up page, select System State. Click Next.
-
When the Backup Type, Destination, And Name page opens, choose the appropriate option in the Select The Backup Type box.
-
Choose the location for the backup in the Choose A Place To Save Your Backup box.
-
Enter a name for the backup job in the Type A Name For This Backup box. Click Next.
-
Click the Advanced button on the Completing The Backup Or Restore Wizard page.
-
When the Type Of Backup page opens, choose the Normal option for the backup type. Click Next.
-
In the How To Back Up page, it is recommended to select the Verify Data After Backup option.
-
If hardware compression is supported, and you are using a tape mechanism, click the Use Hardware Compression, If Available option. Click Next.
-
When the Backup Options page opens, choose Replace The Existing Backups, and choose Allow Only The Owner And The Administrator Access To The Backup Data And To Any Backups Appended To This Medium. Click Next.
-
Select the Now option in the When To Back Up page. Click Next.
-
Click Finish
-
Click the Report button on the Backup Progress page to view a report on the backup job just completed.
Restoring Domain Controllers
When you restore system state data, including Active Directory to a domain controller, you basically have to decide on the method of restore to perform. System state data can be restored on the domain controller by one of the following methods:
-
Nonauthoritative restore: When a nonauthoritative restore is performed, Active Directory is restored from backup media on the domain controller. This information is then updated during replication from the other domain controllers. The nonauthoritative restore method is the default method to restore system state data to a domain controller
-
Authoritative restore: In an authoritative restore, Active Directory is installed to the point of the last backup job. This method is typically used to recover Active Directory objects that were deleted in error. An authoritative restore is performed by first performing a nonauthoritative restore, and then running the Ntdsutil utility prior to restarting the server. You use the Ntdsutil utility to indicate those items that are authoritative. Items that are marked as authoritative are not updated when the other domain controllers replicate to the particular domain controller. Instead, these items are replicated to the other domain controllers.
How to restore system state data on a domain controller – nonauthoritative restore
-
Restart the local computer
-
During startup, press F8 to access the Windows Advanced Options.
-
Proceed to choose Directory Services Restore Mode. Press Enter
-
Choose the operating system that should be started at the Please Select The Operating System To Start prompt. Press Enter
-
Log on to the domain using an account with Administrator privileges.
-
Click OK when a message appears stating that Windows is running in safe mode.
-
Click Start, All Programs, Accessories, System Tools, and then click Backup.
-
When the Welcome To The Backup Or Restore Wizard page opens, click Next.
-
In the Backup Or Restore page, choose the Restore Files And Settings option. Click Next.
-
On the What To Restore page, choose the data that should be restored. Click Next.
-
Verify that the media that contains the backup file is in the proper place.
-
Click Finish to start the nonauthoritative restore.
-
Click OK when a message appears stating that the restore will overwrite existing system state data.
-
When the restore process completes, restart the computer.
How to restore system state data on a domain controller – authoritative restore method
-
You first have to perform a nonauthoritative restore of the system state data to the domain controller. This restore method was outlined in the preceding section.
-
Proceed to restart the computer.
-
During startup, press F8 to access the Windows Advanced Options.
-
Proceed to choose Directory Services Restore Mode. Press Enter
-
Choose the operating system that should be started at the Please Select The Operating System To Start prompt. Press Enter
-
Log on to the domain using an account with Administrator privileges.
-
Click OK when a message appears stating that Windows is running in safe mode.
-
Click Start, and then Command Prompt.
-
Enter and run Ntdsutil.
-
From the Ntdsutil: prompt, insert the following: authoritative restore. Press Enter
-
The authoritative restore: prompt opens next. This is where you specify what you want to restore through its distinguished name. For example, if you want to restore an object, enter restore object. To restore the Active Directory database, enter restore database.
-
Push Enter for the authoritative restore to start.
-
Enter quit to exit out of Ntdsutil.
-
Restart the domain controller and reconnect it to the network.
-
All changes from the other domain controllers that were not marked as authoritative are replicated to this particular domain controller. The changes that are marked as authoritative are replicated from this particular domain controller to the remainder of the domain controllers.

Follow Us!