Honey monkeys are a new way of detecting malicious codes from websites that try to exploit certain vulnerabilities of Internet browsers. The honey monkey system works as an automated web/internet patrol system that is designed to detect harmful materials in the Internet, to be able to come up with solutions, and to catch the people behind these malicious acts.
A Honey monkey is actually a virtual computer system that works by logging on to websites just like a normal computer system or personal computer does. However, it is actually a program designed to detect harmful codes that a certain website might try to inject or silently install onto computers that access it.
Honey Monkey History
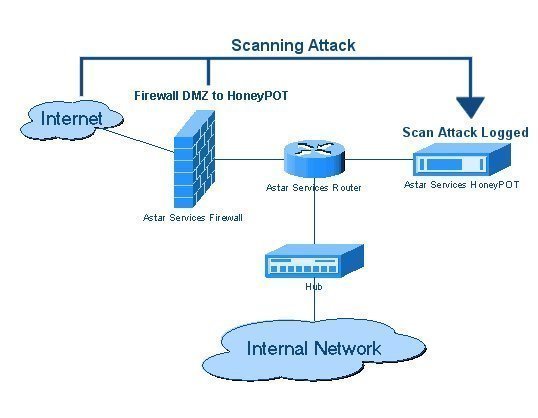
The term "honey monkey" was dubbed by Microsoft from a previous system called "honeypots" which is also a method for detecting such malicious codes from harmful websites. This is where the term "honey" in honey monkeys came from.
Honeypots utilize a passive system or a passive machine to be able to detect harmful codes. Honeypots had the detecting functions of the honey monkeys but they were more passive – they lured in attackers but did not actively look for them – and they collected information mainly for academic and research purposes.
The Honey monkeys, on the other hand, are active participants. The term "monkey" is used because the honey monkey system utilizes a dynamic and a more active way of detecting threats.
How a Honey Monkey Works
Honey monkeys work in a way that is very much similar to those of ordinary home personal computers. They are actually a system of software that mirror real computer systems that consumers or surfers actually use in their homes. This system then forms a kind of virtual computer system that scours and searches the World Wide web for sites that contain harmful codes that could infect the computer systems of unsuspecting visitors.
The websites that the honey monkey system visits will see the system as they would see a normal home personal computer system. The virtual PC system created by Honey Monkeys simulates a computer running on a Windows platform and running under different simulated hardware and software conditions with all the usual weaknesses.
Once the honey monkey system detects malicious code from a certain website, an alarm is sounded and certain logs and reports are made regarding the nature and details of the attack and its originating website.
A certain software system or what they call a strider is used together with the honey monkey system; this is called the strider honey monkeys. This is designed to detect the harmful change that code injection will elicit on an ordinary computer system's settings and parameters.
Honey Monkey Applications
The honey monkey system could be used to help solve problems regarding dangers from any viral or malicious code attacks that could arise from visiting harmful websites. This system could be used to search for and detect such threats and to come up with solutions like patches and infection symptoms which would prepare the public for future attacks.

Follow Us!