Anyone who plays video games knows that they are not cheap. To get around paying for them, many users take advantage of keygen software that is widely available for free on the Internet market and allows users to trick the game into thinking that they have the correct registration key. This type of theft does not stop at games and often extends to other types of software. Many people use these keygens but do not understand how they work. This article will explain what keygens are and how they work.
What is a Keygen
A keygen is a program that allows users to open and use software without paying for it. Keygens use various password-cracking algorithms to find a combination that serves as a correct password, crack the software in order to find a list of correct passwords, or even rewrite parts of the software to create their own correct passwords. Because of their less-than-honest nature, keygens often include viruses, trojans, or worms that infect and damage the user's computer.
Disassembler
A disassembler is a program that converts the machine language of a software into assembly language. Assembly language simply refers to a type of programming language that abbreviates functions and processes so that programmers can remember or figure out how a particular software works. Assembly language generally includes comments by the original programmer and can often include written instructions of how to rewrite the software. Because assembly language includes written text and language that humans can understand, a disassembler is basically a program that allows hackers to conjure instructions on how to hack into a particular software.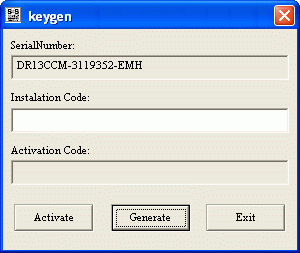
Subroutine
A subroutine is a section of programming code inside of a software that performs a specific task. In effect, a subroutine is a software within a software. In the case of keygens, a subroutine would be the specific section of code within a software that verifies whether a password is correct or not. By hacking into the subroutine of a software, a keygen is able to create its own passwords that the subroutine thinks is correct. Because of this simple task, keygens are able to provide free access to software for millions of computer users worldwide.
Product Activation
One problem that keygens often run into is product activation. Product activation involves the use of ID numbers and product keys that are printed on the material of software, hardware, and other computer appliances. When the user activates his/her product, he/she must enter both of these verification keys in order to use the software. More often than not, product activation also checks the user ID and serial number against the vendor's password database. As this involves a real-time, unique transaction of serial numbers, keygens are often unable to hack software that uses product activation.
Online Key Verification
Similar to product activation, online key verification often stands in the way of a keygen program. Online key verification uses multiple algorithms to ensure that a serial number or product key is not a fake. This works by having the user type in his/her serial number and then checking it against the vendor's database. While the keygen may be able to generate a password based on the algorithm found in the software, a secondary algorithm may be used by the vendor to eliminate certain characters within the serial number. For example, a vendor's secondary algorithm may not allow serial numbers that include the letters A, B, C, or D. The primary algorithm would not include such restrictions so the serial number generated by the keygen software would be false.



Follow Us!