Network Load Balancing Overview
Network Load Balancing (NLB), included in Windows 2000 and Windows Server 2003 can be used if you need to provide increased levels of availability for TCP/IP applications. All versions of Windows Server 2003 include NLB. While NLB is automatically installed, it is not enabled. In a NLB cluster, client requests are load balanced between the servers residing in the NLB cluster, as specified by configured load balancing parameters. Servers can be configured to share the processing of client requests. NLB can also reroute any requests that are sent to a failed NLB cluster server.
Network Load Balancing (NLB) is typically used to provide high availability for Internet applications. This is due to NLB being a clustering technology that works well for traffic based applications. A NLB cluster can host up to 32 servers. Servers in a NLB cluster are called hosts. Each host in the cluster runs a copy of identical application. To clients attempting to access the NLB cluster, the cluster is represented as being one entity. This is made possible by the virtual network adapter created on each host in the cluster. Each virtual network adapter has a unique IP address and MAC address. When a client sends an application request to the cluster, the IP address of the cluster is used, and not each specific host’s IP address. When the client request is received at the cluster, each host in the cluster receives the request. The Network Load Balancing service running on each host determines which host in the cluster should process the request.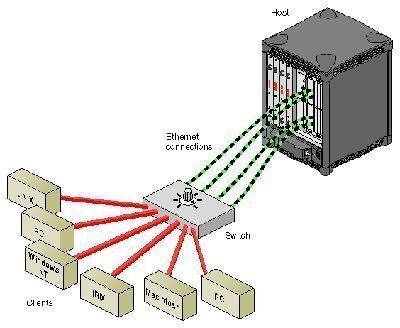
The NLB servers use a statistical mapping that determines a host priority for an incoming packet, to identify the NLB server that should handle the request. Once the NLB server is identified for the packet, the remainder of the servers in the NLB cluster discards the packet. You can though configure a dedicated IP address for network traffic that should be routed to a specific cluster server. Each server in the NLB cluster utilizes and transmits heartbeat messages to identify the state of the cluster. The heartbeat message holds information on the state of the cluster, and the cluster configurations and associated port rules.
Servers in a NLB cluster, as mentioned previously, are called hosts. Each NLB cluster has a default host. The default host is the server in the cluster that has the highest priority. A priority is a unique number assigned to each host in the NLB cluster. The priority determines the handling priority for all requests which are not specifically load balanced according to port rules. The unique host ID also identifies each host in the NLB cluster.
The load weight factor can be used to distribute client requests between the hosts in the NLB cluster. You can configure heavy loads for robust servers, and configure light loads for servers that do not have great processing power. If no load weight is defined, then all servers in the NLB cluster have equal load weights. The lowest weight which can be assigned is 0, and the highest is 100.
Traffic distribution is the terminology used to refer to how client requests are distributed in the NLB cluster. Each server in an NLB cluster has the following IP addresses:
-
Cluster IP address for client requests directed to the cluster.
-
Reserved IP address for traffic explicitly directed to it.
As mentioned previously, all client requests are sent to the cluster IP address, and are received by each host in the NLB cluster. The NLB driver configured for each server in the cluster functions between the network adapter and the TCP/IP protocol. The driver manages and assigns client requests to a server in the NLB cluster based on the specified port rules. Port rules direct traffic on specific ports to certain hosts in the cluster.
The servers in a NLB cluster send heartbeat messages to determine the state of the cluster. Each heartbeat message contains the following information:
-
Information on the state of the NLB cluster.
-
Information on the configuration of the cluster.
-
Information on port rules.
Whenever servers are added to or removed from an NLB cluster, a process known as convergence occurs. Convergence enables the NLB cluster to reconfigure itself so that its configuration can include the server(s) which were added or removed. Convergence also takes place when a server in the cluster does not send a heartbeat message within 5 seconds. During the convergence process, all client requests are still handled by the NLB cluster.
The events which occur during convergence are listed here:
-
The servers which belong to the NLB cluster are determined.
-
The default host is determined.
-
The load weight factor is calculated.
The advantages of NLB clusters are listed here:
-
The NLB cluster can automatically detect when one server has a failure, and then reroutes traffic requests to the other servers in the cluster which are online. This leads to enhanced availability for mission-critical applications.
-
The performance of applications can be scaled because client requests are distributed between multiple servers in the NLB cluster.
-
You can easily add additional servers to an NLB cluster as the network expands. The NLB cluster does not have to be shut down to add or remove servers from the cluster.
-
Client requests to the NLB cluster are load balanced, based on the processing configuration specified for the cluster. You can also configure port rules to specify any servers that should process specific requests.
Understanding Port Rules
Through configuring port rules, you can specify how client requests are processed by the servers in the NLB cluster. A port rule basically acts a filter on a specific port(s). You can specify a protocol parameter and a filtering mode to configure the manner in which traffic must be load balanced between servers in the NLB cluster.
A protocol parameter is used to specify which protocol should be filtered in the particular port range. Requests for the protocol specified in the protocol parameter are affected by the port rule, and all other requests are then handled by the default filtering mode defined in the Host Priority setting.
A port range is used to define the port or set of ports that a port rule is applicable for. Two port ranges that overlap are not allowed.
Each port rule has a filtering mode which indicates how client requests to the NLB cluster are processed by the hosts residing in the cluster.
You can configure the following filtering mode options:
-
Disabled; used to block traffic matching the specified IP address, protocol, and port range from being received at the NLB cluster.
-
Single Host; traffic matching the cluster IP address, protocol and port range is processed by a single host in the NLB cluster.
-
Multiple Host; traffic matching the cluster IP address, protocol and port range is distributed to multiple hosts within the NLB cluster. The Load Weight setting and Affinity setting are used to determine which specific host handles the client request. Affinity relates to how many requests from the same client are distributed between the hosts in the cluster. The Affinity options which you can choose between are:
-
None; indicates that any host in the cluster which matches to the port rule can handle the client request.
-
Single; indicates that one host in the NLB cluster can process traffic from the same client. The requests are basically transmitted to the same host every time NLB reads the IP address.
-
Class C; indicates that all client requests from the identical Class C IP subnet is transmitted to the identical host in the NLB cluster. No lod balancing is performed when this Affinity option is enabled.
-
Planning a NLB Cluster Implementation
A number of NLB installation requirements and few factors which you should consider are listed here:
-
Windows 2000 Advanced Server, or any Windows Server 2003 Edition.
-
The TCP/IP protocol.
-
Fiber Distributed Data Interface (FDDI), Ethernet or Gigabit Ethernet
-
1.5 MB available hard disk space
-
4MB – 250 KB RAM
-
You should have two network adapters for each cluster host.
-
The hosts residing in the NLB cluster should exist in the same physical subnet.
-
The applications which you plan to add to the NLB cluster must be capable of using TCP or UDP ports.
-
Clients must be able to connect to the NLB cluster using TCP/IP.
-
You should plan server capacity based on the types of applications which you plan to add to the NLB cluster.
-
You should add servers to the NLB cluster until the expected client request load can be handled by the cluster. Be careful to not overload the cluster.
-
You need to ensure that the servers in the NLB cluster can support the applications hosted on them. The servers should be properly configured to run the applications which they host. With NLB, all applications that can be configured to use TCP/IP with the appropriate port can be configured for load balancing. Applications supported in a NLB cluster include FTP, TFTP, SMTP, HTTP, and HTTPS.
When planning the NLB cluster you should include elements that are geared at increasing the availability of the NLB cluster:
-
Eliminate all probable points of failure.
-
Use uninterruptible power supplies.
-
Ensure redundant access to the WAN.
-
Only load balance suitable applications.
-
Configure servers correctly to run the applications hosted on them.
A few factors that you need to determine before you can implement a NLB cluster are listed here:
-
Determine the IP address and subnet mask for the cluster.
-
Determine the Internet name for the cluster.
-
Decide whether the cluster is going to operate in multicast mode or in unicast mode.
-
For each host to be added to the NLB cluster, determine its priority.
-
For remote operation, decide on the password.
-
Decide on the handling priority.
-
Determine your port rules and the port range which you are going to use.
-
Decide on the filtering mode.
-
Decide on the protocols.
-
Determine which affinity option you will be using.
Securing an NLB Cluster
A few strategies for securing an NLB cluster are listed here:
-
Physically secure the servers of the cluster.
-
Restrict physical access to the cluster infrastructure.
-
All mission critical server clusters should be placed behind firewalls.
-
Use the firewall configuration to control traffic that is directed to the cluster.
-
The security features of applications hosted in the NLB cluster should be used to further secure the NLB cluster.
-
You should use a unique account to administer each individual cluster. This would ensure that if one account is compromised, it cannot be used on all clusters.
-
You should regularly audit activities on the NLB cluster.
How to create a NLB cluster
-
Click Start, click Administrative Tools, and then click Network Load Balancing Manager.
-
Click the Cluster menu item and then select New.
-
In the Cluster IP configuration area of the Cluster Parameters dialog box, specify the IP address, subnet mask and full Internet name for the new NLB cluster.
-
In the Cluster operation mode section are of the Cluster Parameters dialog box, select the mode for the cluster.
-
On the Cluster IP Addresses dialog box, click the Add button if you want to load-balance multiple IP addresses. Click Next.
-
On the Port Rules dialog box, the default port rule is displayed. Click the Edit button to configure port rules.
-
The Add/Edit Port Rule dialog box opens. You can add and remove port rules.
-
Click Next on the Port Rules dialog box.
-
On the Connect dialog box, provide the name of the host in the Host field and then click the Connect button.
-
Specify the network interface which should be load balanced. Click Next.
-
On the Host Parameters dialog box, specify the Priority, Dedicated IP address and Subnet Mask information for the host.
-
Set the Default State of the host to Started.
-
Click Finish.
-
The Network Load Balancing Manager opens, displaying the new cluster.
Troubleshooting NLB clusters
You can use the Network Load Balancing Manager to view log entries created by activities of the NLB cluster.
The NLB log entries provide information on the following:
-
Changes made to the configuration of the NLB cluster.
-
Errors which resulted from the incorrect configuration settings of a host residing in your NLB cluster.
A few strategies for troubleshooting NLB clusters are summarized below:
-
If there is an IP address conflict after NLB is installed:
-
Verify that the same primary IP address is configured for each host contained in the NLB cluster.
-
If you are running NLB in unicast mode, check whether the network adapter’s network address has changed. You might need to change to multicast mode, or change the existing network adapter.
-
-
If you have an application running on a cluster host which does not operate correctly, the issue is probably due to the port(s) of the application being load balanced. Ensure that your port rules include only those applications which should be load balanced.
-
If the default cluster host is processing all client requests, ensure that the ports used by an application are included in port rules. With NLB, all traffic which are not impacted by port rules, end up at the default cluster host.
-
If you have an application configured to be load balanced that does not operate correctly:
-
Verify that the problematic application is running on all hosts residing in the NLB cluster. Applications have to be manually started.
-
Verify that the application can indeed be load balanced.
-
Verify that the application is configured to use the TCP/IP protocol.
-
Verify that all ports used by the application are load balanced.
-
Verify that the defined port rules include each port used by the application.
-
Verify that Affinity is enabled, and specified as either the Single option or Class C option.
-
- For applications to be load balanced in an NLB cluster, the application has to meet the following requirements
-
- TCP ports or UDP ports must be used by the applications
-
Multiple instances of the application should be simultaneously capable of running.
-
Clients must connect through TCP/IP.
-
Affinity must be enabled, with either of the following options: Single option or Class C option.
-
If a host in the cluster starts to converge but fails to complete the process:
-
Verify that the port rules are compatible.
-
Verify that the same port rules exist on all hosts in the cluster.
-
-
If after the NLB convergence process, more than one default host exists in the NLB cluster:
-
Verify that the primary IP address is configured identically on each host within the NLB cluster.
-
Verify that th primary IP address of the cluster is specified in the TCP/IP properties.
-
The issue might also be due to hosts being inaccessible on the network, typically because they are located on different subnets.
-
-
If a host in the NLB cluster does not respond to a remote command:
-
Verify that the remote computer is on the correct subnet.
-
Verify that the UDP control ports are not being blocked by a firewall configuration.
-
Verify that the command was sent to the cluster’s primary IP address.
-


Follow Us!