An Overview on Authentication and Smart Cards
Administrators have to secure the network from attacks launched by hackers, spies, terrorists, thieves and criminals. Security encompasses numerous technologies, protocols, standards, policies, passwords, and secret keys. All these mechanisms typically focus on the following:
-
Authentication
-
Access Control
-
Data Protection
-
Auditing/Accountability
Authentication is the process by which an entity identifies itself, before network logon is permitted. After a user is authenticated, access control defines what resources can be accessed, what actions can be performed on the resource, and whether these actions are audited or not. Access control is implemented by specifying permissions for resources and objects, and assigning rights to users. Data protection involves two security concepts, namely, data confidentiality, and data integrity. Data confidentiality deals with securing data as it is transmitted over the network through the application of cryptographic operations. Encryption algorithms and the utilization of private and public keys provide data confidentiality. Any unauthorized parties intercepting the message, will not be able to interpret the contents of the message. Data integrity is implemented through the digital signing of messages, and files. Through the use of digital signatures, you can determine whether the message was tampered with or not. From this brief discussion, you can see that many concepts and principals are included when discussing security. So where does smart cards fit into the process of securing an organization's network and resources from malicious attacks. The answer is authentication.
As mentioned earlier, authentication is process whereby which users or other entities identify themselves so that they can attempt to access network resources. Authentication is the initial step in the process of allowing users to access network resources. In Active Directory, user authentication occurs by the user providing user account credentials, such as the user logon name, password, and the user's security identifier (SID).
Authentication in Windows Server 2003 environments involves the following two processes:
-
Interactive logon: Interactive logon occurs when a user logs on to the system using a password or smart card.
-
Network authentication: Network authentication occurs when a user is permitted to access resources, without the user having to re-enter this password or the personal identification number (PIN) of the smart card.
The user or entity proves its identity by using a shared secret. The shared secret can be one of the components listed below, and has to be a secret between the user requesting authentication, and the authenticator, for authentication to be successful:
-
A password
-
An encryption key
-
A secret PIN
Authentication protocols are used to share the secret between the user and authenticator. The authenticator then either allows access or denies the requestor access. The authentication protocols that can be used in Windows Server 2003 environments are listed below:
-
Kerberos version 5, used for network authentication. Kerberos version 5 is used for the interactive logon authentication process, and for network authentication in Windows Server 2003.
-
Secure Socket Layer/Transport Layer Security (SSL/TLS), used for network authentication and is based on X.509 public key certificates.
-
Microsoft Windows NT LAN Manager (NTLM), used for network authentication but mainly for Microsoft Windows NT 4 compatibility.
-
Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2), used for network authentication and dial-up authentication.
-
Password Authentication Protocol (PAP), used for network authentication and dial-up authentication.
-
Extensible Authentication Protocol-Transport Level Security (EAP-TLS), used for wireless connection authentication.
-
Extensible Authentication Protocol (EAP), used for network authentication and dial-up authentication, and includes support for smart cards (hardware enabled authentication).
Hardware enabled authentication occurs when encryption keys are stored on a smart card, a PC card, or some other cryptographic token mechanism, and the user needs to have the smart card, and the PIN or password to pass authentication and access the system. This provides an additional level of security because any unauthorized individuals attempting to access the system, needs the smart card and the PIN or password.
Smart card authentication is based on the use of smart cards and is supported in Windows 2000 and Windows Server 2003. A smart card is a security device or credit card sized hardware token which can be used to provide additional protection to applications and security protocols.
Smart cards provide the following features:
-
Secure method of user authentication
-
Interactive logon
-
Remote access logons
-
Administrator logons
-
Secure code signing
-
Secure e-mail
In network environments, they are typically used for following purposes
-
Logging on to a computer
-
Encryption of e-mail
-
Encryption of disk files through EFS
As mentioned earlier, smart card authentication provides very strong authentication because the user has to possess the smart card, and the user has to know the personal identification number (PIN). You can block a smart card from the system after a successive number of unsuccessful logon attempts have been made. To enable these features, smart card authentication involves the use of a smart card reader which is attached to the computer. It is recommended to use Plug and Play (PnP) readers with Windows Server 2003. The smart card contains a microprocessor and permanent flash memory that holds the user's logon information, private key, digital certificates, and other private information. When the user inserts the smart card into the smart card reader, the user has to provide the PIN to log on to the system. Smart cards are designed to provide tamper-resistant authentication. The difference between smart cards and software private keys is that you can move smart cards from one computer to computer.
The smart card reader is usually attached to the serial port, USB port, or PCMCIA port of the computer. Since PCs, laptop computers, and PDAs have one of these ports, smart card readers are supported by all computers. Smart cards are available in a number of forms. The majority though have a resemblance to credit cards. The more advanced smart cards utilize magnetics. What this means is that they do not need to have external contacts. A common form is the dongle which can fit into a USB port. From here, it is accessed by the Cryptographic Service Provider (CSP). The dongle form does not need any special reader. The downfall of the form is that it is roughly four times more costly than the conventional smart card forms. While the installation of a smart card implementation can be complex and expensive, another difficult process is determining which vendor to use. The drivers of smart card products from Gemplus and Schlumberger are actually built into the operating system.
Smart Card Deployment Considerations
Authentication through smart cards is supported in Windows 2000 and Windows Server 2003, but is dependent on the Public Key Infrastructure (PKI). The PKI has to exist before you can implement smart card authentication. It is recommended to use an enterprise certification authority (CA) for authentication based on smart cards. Stand-alone CAs and external CA entities are not recommended for use with smart card authentication.
While there are quite a number of vendors to choose from to provide your smart card technology, remember that Windows Server 2003 does not support on-Plug and Play smart card readers. It is recommended to only use Personal Computer/Smart Card (PC/SC) compliant smart cards and readers, even when a vendor provides non-Plug and Play smart card readers that can operate with Windows Server 2003. In addition to the implementation of a PKI, each computer needs a smart card reader.
Because cost is always an important factor, you can consider the factors listed below as those that affect the cost of administering a smart card implementation:
-
The number of users that will use the smart card program, as well as where these particular users are located.
-
The manner in which the users are going to be issued smart cards. The requirements for verifying user identities should also be included.
-
The procedure to be used when users misplace or damage the smart cards which were issued to them.
When planning a smart card authentication solution, you have to define the authentication and logon methods which are going to be utilized. This would include:
-
Identifying the authentication strategies which are going to be implemented.
-
PKI dependencies.
-
Any smart card deployment issues.
Preparing the PKI for a Smart Card Implementation
As mentioned earlier, smart cards are dependent on the implementation of a PKI. Smart cards need certificates to manage which users are allowed to authenticate using smart cards. Certificates are used to verify the identities of users, applications, computers, and services; and can be used to secure e-mail, for Web and application code authentication, and to enable the use of smart cards. A certificate authority (CA) issues certificates to users and other entities.
The certificate would usually contain the following information:
-
The serial number of the certificate
-
Information that identifies the user.
-
Information that identifies CA that issued the certificate.
-
The user's public key
-
The validity period of the certificate
-
The distinguished name of the issuing CA server
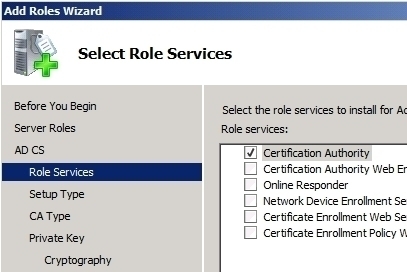
The ability of the PKI to support smart cards is an attractive feature of the Windows PKI implementation. To implement smart cards, one of the first steps is to install certificate services on a server within your environment, and configure the server as an enterprise CA. After this, you would need to create three certificate templates to enable the use of smart cards within your organization. Certificate templates can be defined as a set of rules and settings which specify the content and format of certificates that are issued, based on intended use. You configure certificate templates on the CAs within your PKI implementation. The certificate template is applied when a user requests a certificate from the CA. Only Windows Server 2003 enterprise CAs utilizes certificate templates stored in Active Directory to create certificates for users and computers.
For a smart card implementation, you need to create the following three certificate templates:
-
Enrollment Agent Certificate: This certificate template enables a Windows Server 2003 computer to serve as an enrollment station. The enrollment station creates and issues certificates to smart card users.
-
The Smart Card Logon Certificate: This certificate template enables users to authenticate using smart cards.
-
Smart Card User Certificates: This certificate template enables users to secure e-mail after authentication.
Implementing Smart Cards
The typical steps for implementing a smart card solution in an organization are listed below. The actual steps are determined by the manner in which smart cards are used in the PKI:
-
Configure an enrollment station
-
Define the necessary certificate templates for the CA and Active Directory.
-
Define enrollment agents who will issue smart cards
-
Prepare the smart cards
-
Issue certificatesto the smart card for users
-
Configure remote access servers to accept smart card authentication
-
Enroll the servers for Computer certificates
Because the certificate templates used by smart cards are not installed on an enterprise CA by default, you will need to use the Certification Authority console to configure these certificate templates. In addition to this, you need to assign users the correct permissions for the certificate templates. To change permissions for a certificate template, you need to be a member of the Domain Admins group in the forest root domain, or a member of the Enterprise Admins group.
How to set permissions on certificate templates
-
Click Start, Run, and enter certtmpl.msc in the Run dialog box. Click OK.
-
Locate and right-click the certificate whose permissions you want to modify, and then click Properties on the shortcut menu.
-
Click the Security tab.
-
Assign users and groups who need to request certificates that are based on the particular certificate template, the Read and Enroll permissions.
-
Click OK.
The certificate server included in Windows Server 2003 includes a smart card enrollment station which can be used to distribute certificates to users. You can use the smart card enrollment station to request a smart card certificate on a behalf of the user. This in turn enables you to preinstall it on the smart card of the user. Before users can request certificates, you need to prepare the enrollment station to create the certificates. The first step in preparing the CA to issue smart card certificates is to create the Enrollment Agent certificate.
How to create the Enrollment Agent certificate
-
Click Start, Administrative Tools, and then click Certification Authority.
-
In the console tree, expand Certificate Authority, <Server name>, and Certificate Templates.
-
Click New, and then Certificate to Issue from the Action menu.
-
Choose Enrollment Agent template. Click OK.
-
On the Action menu, click New, and then Certificate to Issue from the Action menu
-
If you want to create certificates for user authentication, choose the Smart Card Logon certificate template. Click OK.
-
If you want to create certificates for user authentication, and for the encryption of the user's information, choose the Smart Card User certificate template. Click OK.
-
-
The certificate templates should now be displayed in the console window
-
Close the Certification Authority console.
How to create a smart card certificate enrollment station
-
Log on to the machine
-
Click Start, Run, and enter mmc in the Run dialog box. Click OK
-
From the File menu, click Add/Remove Snap-in, and then click Add.
-
Double-click the Certificates snap-in. Click OK.
-
Click Close.
-
In the Certificates snap-in, expand Certificates, Current User, and then Personal.
-
Select All Tasks, and then Request New Certificate from the Action menu.
-
When Certificate Request Wizard starts, click Next.
-
When Certificate Types page opens, click Enrollment Agent and then click Next.
-
On Certificate Friendly Name and Description page, enter a description for the certificate. Click Next.
-
When the summary page opens, click Finish.
Setting up users to utilize smart cards includes the purchase and installation of smart card readers for all user workstations. Installing smart card readers that are Plug and Play compatible is usually an uncomplicated hardware installation.
The smart card readers supported by Windows XP and Windows Server 2003 are listed below.
-
American Express, GCR435 – USB port
-
Bull, SmarTLP3 – serial port
-
Compaq, Serial reader – serial port
-
Gemplus, GCR410P – serial port
-
Gemplus, GPR400 – PCMCIA port
-
Gemplus, GemPC430 – USB port
-
Hewlett-Packard, ProtectTools, – serial port
-
Litronic, 220P, – serial port
-
Schlumberger, Reflex 20 – PCMCIA port
-
Schlumberger, Reflex 72 – serial port
-
Schlumberger, Reflex Lite – serial port
-
SCM Microsystems, SCR111 – serial port
-
SCM Microsystems, SCR120 – PCMCIA port
-
SCM Microsystems, SCR200 – serial port
-
SCM Microsystems, SCR300 – USB port
-
Systemneeds, External – serial port
-
Omnikey AG, 2010 – serial port
-
Omnikey AG, 2020 – USB port
-
Omnikey AG, 4000 – PCMCIA port
Some smart card reader's drivers are preinstalled in Windows Server 2003, while others are not. You can install a smart card reader on the computer by attaching the smart card reader to a serial port or USB port. For laptops, insert the smart card reader into a PCMCIA slot.
After the smart card reader is installed, the Enrollment Station must be used for the following tasks:
-
Install smart card logon or user certificates for your users' smart cards.
-
Set the initial PIN for the user.
When the smart card readers are installed, the next step is to issue smart card certificates to users. This process is known as enrollment. Before enrolling a user, and issuing the user with smart card, you should educate users on these points:
-
Users should refrain from bending the smart card because they can damage the internal mechanisms of the smart card.
-
Users should protect the external smart card chip from being scratched or dented. The smart card reader might be unable to read the information stored on the card if it is damaged in this way.
-
Users should store their smart cards in a cool dry location, and safe from any other magnetic sources such as credit cards. Excessive hot temperatures could result in the smart card becoming brittle and breakable.
To enroll a smart card user,
-
Access the workstation using a user account which has the necessary rights in the Enrollment Agent Certificate template for the domain containing the user account.
-
Open Internet Explorer, and access the CA by entering http://CA server name/certsrv.
-
On the Welcome page, click Request a Certificate
-
On the Request a Certificate page, click Advanced Certificate Request.
-
On the Advanced Certificate Request page, choose the Request a Certificate for a Smart Card on behalf of another user option.
-
On the Smart Card Certificate Enrollment Station page, choose to create one of the following:
-
Smart card logon certificate
-
Smart card user certificate
-
-
In the Certificate Authority list box, choose the name of the CA for the domain that should issue smart card certificates.
-
In the Cryptographic Service Provider list box, enter the name of the vendor which you are using for smart cards.
-
In the Administrator Signing Certificate box, enter the name of the enrollment Agent certificate which will sign the certificate enrollment request. Click Next.
-
On the User to Enroll page, click Select User to find the user account that you want to create a smart card certificate for, and the click Enroll.
-
Place the smart card of the user in the smart card reader, and click OK.
-
Proceed to enter the initial PIN for the smart card.
-
Click View Certificate to verify that the certificate was issued to the user which you specified.
A Windows 2000 or Windows Server 2003 remote access server supports smart card logon. To enable smart card logon for these servers, you have to configure the RRAS service to use the Extensible Authentication Protocol (EAP). Then, you have to specify smart card logon as the EAP method.
To configure a Windows 2000 or Windows Server 2003 remote access server for smart card logon,
-
Open the RRAS console from Administrative Toos.
-
Proceed to open the Properties dialog box of the remote access server that should accept smart card logon.
-
Click the Security tab.
-
Click Windows Authentication, and click Authentication Methods.
-
Choose the Extensible Authentication Protocol (EAP) option.
-
Click EAP Methods.
-
Use the available list to find and double-click Smart Card or Other Certificate. Click OK.
-
Proceed to deselect the other authentication options. Click OK.
-
In the Properties dialog box of the server, click OK.
-
In the RRAS console, locate Remote Access Policies in the console tree.
-
Double-click Allow Access If Dial-In Permission Is Enabled.
-
When the Properties dialog box open, click Edit Profile.
-
Click the Authentication tab.
-
Click EAP Methods.
-
When the Select EAP Providers dialog box opens, click Add.
-
In the Add EAP dialog box, choose the Smart Card or Other Certificate option.
-
Click OK.
-
In the Select EAP Providers dialog box, Click Edit.
-
When the Smart Card or Other Certificate Properties dialog box opens, in the Certificate Issued To box, choose the computer certificate issued to the particular server.
-
Click OK, and close all open dialog boxes.
You can enable certain policy settings in Group Policy that can assist in simplifying smart card administration in your environment:
-
Account lockout threshold: You can use the settings of this policy to protect your smart card authentication process from password attacks.
-
Do not allow smart card device redirection: When enabled, users will not be able to use smart cards to log on to a Terminal Services server.
-
On smart card removal: You can use this setting to prevent users running unattended active sessions. Use these settings to specify that the users' sessions are locked, or logged off when they remove their smart cards from the smart card reader.
-
Smart card required for interactive logon: When enabled, a user can only log on to the local computer using smart card authentication. The user cannot use a user account and provide the user name and password credentials to log on.



Adi
Hi, I am using windows XP sp3. Today, by accident, I enable interactive smart card logon on group policy editor. So I cant logon anymore to my machine because it is said that smart card be required for logon therefore I dont have valid smart card. Do you know how to disable this feature without logon to XP? Do you have any sollution? Please let me know by email.
Thanks