Internet Security and Acceleration Server (ISA Server) Overview
Microsoft Internet Security and Acceleration Server (ISA Server) is combination of a firewall and Web caching server that can be used to protect the enterprise from external access, while sharing a internet connection on the network. The multilayer firewall of ISA Server protects valuable network resources of the enterprise from unauthorized external access, attacks from hackers, and malicious viruses. You can also control client access to the Internet. The Web cache server enables faster Web access for users by serving objects locally from the cache instead of over the Internet. This in turn improves Internet performance for clients on the network.
The internal private network is separated from the Internet. There is one physical connection to the Internet and another to the internal network. The networks are also connected to different network cards. Traffic must move through the ISA Server software to move from one connection to the other.
When you install ISA Server in your network, you can configure it as:
- A firewall that controls inbound access and outbound access through filters and rules, and various other configuration settings.
- A Web cache server that manages outbound access through rules, and downloads and caches frequently accessed data.
- A firewall and Web cache server.
The architecture that ISA Server uses to protect the private network from unauthorized access and still enable users to access the Internet are listed here:
- The ISA Server Firewall service provides in-bound protection and management of protocol specific filters.
- The ISA Server Web Proxy service provides outbound access.
- The clients and servers hosted on the private network that need to access the public network. These include:
- Web proxy clients.
- SecureNAT clients.
- Firewall clients.
- Web servers.
- mail servers.
- The clients and servers hosted on the private network that do not want to access the public network nor be accessed by the public network.
- The Internet.
ISA Server Firewall Service Overview
The ISA Server firewall technology consists of a number of firewall techniques that secure the network from unauthorized access:
- Packet filtering.
- Circuit-level (protocol) filtering.
- Application-level filtering.
- Stateful inspection.
- Built-in intrusion detection.
- System hardening templates.
- Virtual Private Networking.
With packet filtering, you can manage the flow of IP packets to ISA Server and from ISA Server. Packet filtering inspects the header of each packet for protocol, port, and destination address and source address information. Packets are dropped if they are not explicitly allowed.
When you configure circuit-level (protocol) filtering, sessions are inspected, and not packets and connections. You can use access policy rules and publishing rules to configure circuit-level (protocol) filtering. ISA Server supports dynamic filtering. With dynamic filtering, ports open automatically only when needed, and closed once communication has occurred. In this manner, the number of ports that remain open are reduced. Circuit-level filtering provides integrated support for protocols with secondary connections. You can configure the primary and secondary connection of the protocol in the user interface. This is done by specifying the following:
- Port or port range.
- Protocol type.
- Transmission Control Protocol (TCP) or User Datagram Protocol (UDP)
Inbound or outbound direction.
Application-level filtering is used to protect against DNS server attacks and unsafe SMTP commands. You can use third-party tools for content screening and virus detection to apply application and Web filters. Withapplication-level filtering, the data stream for an application is analyzed and inspected, and can be blocked, redirected, or modified.
ISA Server provides the following application filters:
- HTTP Redirector Filter; forwards HTTP requests to the Web Proxy service, from the firewall and SecureNAT clients.
- FTP Access Filter; intercepts and inspects FTP data.
- SMTP Filter; intercepts and inspects SMTP traffic. The SMTP filter can screen e-mail messages for content or size, and can also detect unsafe SMTP commands. Any e-mail traffic that is not approved is dropped efore it can reach the mail server. This protects mail servers from being attacked.
- SOCKS Filter; used for clients that do have Firewall Client software. The SOCKS filter sends requests from SOCKS 4.3 applications to the Firewall service, where access policy rules determine whether the SOCKS client application is allowed to communicate with the Internet.
- RPC Filter; inspects and filters RPC requests based on the specific interfaces defined.
- H.323 Filter; handles H.323 packets utilized for multimedia communications and teleconferencing by providing call control capabilities.
- Streaming Media Filter; supports industry-standard media protocols such as Microsoft Windows Media Technologies, Progressive Networks Audio (PNA) and Real-Time Streaming Protocol (RTSP). Users can split live Windows Media streams, thereby conserving bandwidth.
- DNS Intrusion Detection Filter; prevents internal servers from being attacked.
- POP Intrusion Detection Filter; prevents internal servers from being attacked.
ISA Server includes a built-in intrusion-detection mechanism that can protect the network from several common attacks. The built-in intrusion-detection mechanism can be configured to send an alert when an intrusion is detected.
ISA Server implements intrusion-detection at the following levels:
- Packet filter level.
- Application filter level.
ISA Server can detect attacks at the packet filter level:
- All Ports Scan Attack; an attacker is attempting to access more than the configured number of ports. Port scanning or simply scanning, is the process whereby which intruders collect information on the network services on a target network. Here, the intruder attempts to find open ports on the target system.
- Enumerated Port Scan Attack; the unauthorized intruder uses a number of methods to collect information on applications and hosts on the network, and to count the services running on a computer. The intruder probes the ports for a response.
- IP Half Scan Attack; the attacker makes numerous connection attempts to a computer, but does not actually log on. The purpose of the attack is to probe for open ports.
- Land Attack; TCP SYN packets are sent with a spoofed source IP address and port number that match the destination IP address and port number.
- Ping of Death Attack; a large amount of information is appended to a internet Control Message Protocol (ICMP) echo request (ping) packet in an attempt to cause a kernel buffer overflow and crash the computer.
- UDP Bomb Attack; UDP packets that contain illegal values in certain fields are sent in an attempt to cause older operating systems to crash.
- Windows Out of Band Attack; a denial-of-service attack against an internal computer protected by ISA Server.
You can configure POP and DNS intrusion detection filters to check for the following:
- DNS Hostname Overflow.
- DNS Length Overflow.
- DNS Zone Transfer from Privileged Ports (1-1024).
- DNS Zone Transfer from High Ports (above 1024).
The ISA Server intrusion-detection mechanism also allows you to define what action should be implemented by the system when an attac is detected:
- Stop the Firewall service.
- Send an e-mail message to the administrator.
- Record the event in the Windows 2000 Event Log.
- Run a program or script.
You can use the ISA Server Security Configuration Wizard to apply system security settings to servers. You can choose between the following levels of security:
- Secure; ISA Servers are combined with IIS servers, SMTP servers, or database servers.
- Limited Services; ISA is running in integrated mode and could be protected by another ISA Server.
- Dedicated; ISA is a dedicated firewall.
ISA Server can also operate as the end-point for a Virtual Private Network (VPN). A VPN enables data to be sent between computers over public network. VPNs extend the private network by creating a secure link between two separate networks over the Internet. Virtual Private Networks (VPNs) provide secure and advanced connections through a non-secure network by providing data privacy. Private data is secure in a public environment.
Many companies supply their own VPN connections via the Internet. Through their ISPs, remote users running VPN client software are assured private access in a publicly shared environment. By using analog, ISDN, DSL, cable technology, dial and mobile IP; VPNs are implemented over extensive shared infrastructures. Email, database and office applications use these secure remote VPN connections. You can configure ISA Server as a VPN server. You can configure ISA Server to allow VPN traffic from external VPN clients to pass over the firewall to a VPN server on the internal network. You can also configure ISA Server to allow VPN traffic from internal VPN clients to pass to a VPN server on the external network.
A VPN gateway, also called a VPN router, is a connection point that connects two LANs which are connected by a nonsecure network such as the Internet. A VPN gateway connects to either a single VPN gateway, or to multiple VPN gateways to extend the LAN. Tunneling is the terminology utilized to describe a method of using an internetwork infrastructure to transfer a payload. Tunneling is also known as the encapsulation and transmission of VPN data, or packets. The VPN tunnel is the logical path or connection that encapsulated packets travel through the transit internetwork. The tunneling protocol encrypts the original frame so that its content cannot be interpreted. The encapsulation of VPN data traffic is known as tunneling.
A few enterprise firewall security features and benefits of ISA Server are summarized here:
- Stateful inspection; ISA Server can dynamically examine traffic crossing the firewall.
- Application filtering; traffic can be accepted or rejected, redirected and modified based on content through intelligent filtering of:
- HTTP.
- FTP.
- Simple Mail Transfer Protocol (SMTP) e-mail.
- H.323 (multimedia) conferencing.
- Streaming media.
- Remote Procedure Call (RPC).
- Intrusion detection; ISA Server includes intrusion detection based on Internet Security Systems (ISS) technology.
- You can save bandwidth by using streaming media filters.
- ISA Server provides support for secure VPN access to the corporate private network through the Internet.
- ISA Server can provide secure server publishing and Web server publishing capabilities. Web publishing rules protect internal Web servers.
- You can use the Security Configuration wizard to harden the system.
- ISA Server supports strong authentication with its support for Windows authentication methods such as Kerberos and NTLM, and support for client certificates.
ISA Server Web Caching Overview
ISA Server includes the Web Proxy service that can be used to cache frequently requested Web objects. Subsequent client requests are checked against the cache to see if they can be serviced from the cache. A new request is initiated if the ISA Server cache cannot beutilized to serve the client request. ISA Server stores most frequently accessed items in RAM. The items are then retrieved from memory instead of from disk.
Objects remain in the ISA Server cache until either of the following events occurs:
- A more up to date version of the cached object is obtained.
- Space is required for other more recently requested objects.
ISA Web Server caching can be implemented using either of these methods:
- Forward Web caching.
- Reverse Web caching.
- Scheduled caching.
- Distributed caching.
- Hierarchical caching (chaining).
When you configure ISA server as a forward Web caching server, internal clients are able to access the Internet, and ISA Server maintains a cache of frequently requested Internet objects which can be accessed by any Web browser behind the firewall. Client browser performance is improved because using the cache results in less processing than requesting objects from the Internet. Bandwidth usage on Internet connections remains low. User response time is decreased as well.
How forward caching works
- A user requests a Web object.
- The request is forwarded to the ISA Server computer on the network.
- ISA Server checks whether the object exists in the cache.
- If the requested Web object does not exist in the cache, the request is forwarded to a server on the Internet.
- The server on the Internet returns the requested object to the ISA Server.
- The ISA Server places the Web object in its cache.
- The ISA Server forwards the object to the user that requested it.
- When another user requests the same object, the request is forwarded to the ISA Server computer, and the ISA Server computer returns the object to the user from its cache.
With reverse caching, objects requested from internal servers by external clients are stored on the ISA Server. Incoming Web requests are forwarded to the ISA Server and are serviced from the cache. Requests are only forwarded to the Web server when the cache cannot be used to serve the request.
How reverse caching works
- A request is sent to the ISA Server.
- ISA Server checks whether the object exists in the cache.
- If the requested object does not exist in the cache, the request is sent to the Web server.
- The home page is returned to the ISA Server.
- The ISA Server places the object in its cache.
- The home page is forwarded to the person that requested it.
- Another request is sent for the same Web page.
- ISA Server checks whether the object exists in the cache, and returns it from its cache. The request is not sent to the Web server.
You can use the ISA Server Scheduled Content Download feature to download the content to the ISA Server cache as per a predefined schedule. You can proactively ensure that important content is always available directly from the ISA Server cache and that the information is current.
You can directly download the following to the ISA Server cache:
- A single URL.
- Multiple URLs.
- Entire Web site.
You can also limit which content should be downloaded. You can define scheduled content downloading for outgoing Web requests and for incoming Web requests.
The ISA Server Enterprise Edition uses Cache Array Routing Protocol (CARP) to provide scaling and improve efficiency. When you install multiple ISA Server computers, ISA Servers are automatically installed in arrays. The array of ISA Servers is then treated as a single logical cache. A hashing algorithm determines the location for storage, and hash-based routing is used to retrieve the location of the stored object when requests are made.
The advantages of using CARP include:
- By using hash-based routing, CARP ends up becoming more efficient as additional servers are added to the array. This provides enhanced scalability.
- CARP can efficiently locate previously stored content – content duplications are avoided and do not occur.
- With CARP member servers are represented as a single logical cache.
- You can define a load factor for each array server. You can also distribute content evenly over the array.
- CARP can automatically adapt to modifications made to the array, such as adding or removing array members, and taking array members offline and bringing them back online again.
The routing algorithm used by CARP works as follows:
- The array membership list is used to track the status of the servers. The array membership list is updated using the TTL countdown which detects all active proxy servers.
- A hash function is calculated for the name of each particular server.
- A hash function is also calculated for the name of each particular URL requested.
- The hash values of each of the above calculations are joined.
- The owner of the information cache is the highest value derived from combining the server hash value and the hash value of the URL.
- Subsequent requests for the cached information will use the same location.
The ISA Server Enterprise Edition enables administrators to arrange individual ISA Server computers or arrays of ISA Servers hierarchically. This process is also referred to as chaining. Requests are then sent upstream through the chain of servers until the object which was requested is located. Chaining provides fault tolerance. Content can be distributed to multiple locations without making requests on the Internet.
The Different ISA Server Editions and ISA Server Roles
The different ISA Server editions are:
- ISA Server Enterprise Edition: Provides integration with the Active Directory and additional benefits and features such as centralized server management, multiple levels of access policy, server clustering through arrays, fault-tolerant, and the increased efficiencies of hierarchical and distributed caching.
- ISA Server Standard Edition: Provides firewall security and Web caching features for small business, departmental environments, and workgroups.
The following features are the same for both ISA Server editions:
- Security capabilities.
- Caching capabilities.
- Management capabilities.
- Performance capabilities.
- Extensibility capabilities.
The features available with the ISA Server Standard Edition is listed here:
- Firewall, caching, or integrated modes.
- Hierarchical Caching.
- Array Based Policy.
- H.323 gatekeeper.
- Intrusion detection.
- Packet filtering.
- Message Screener.
- Web publishing.
- Server publishing.
- Bandwidth control.
- Logging and reporting.
The features available in the ISA Server Enterprise Edition are listed here:
- Active Directory Integration.
- Firewall, caching, or integrated modes.
- Distributed Caching.
- Hierarchical Caching.
- Array Based Policy.
- Enterprise Policy.
- H.323 gatekeeper.
- Intrusion detection.
- Packet filtering.
- Message Screener.
- Web publishing.
- Server publishing.
- Bandwidth control.
- Logging and reporting.
For each ISA Server edition, you can install ISA Server in either of these installation modes:
- Firewall.
- Caching.
- Integrated.
The different server roles that you can configure for ISA Server are:
- Dedicated firewall.
- Secure Publishing server.
- Forward Web cache server.
- Reverse Web cache server.
- Integrated Firewall and Web Cache server.
Understanding ISA Server and Windows Integration
The Windows technologies that can be used with ISA Server to provide enhanced security, better performance, and management capabilities are listed here:
- If you deploy ISA Server Enterprise Edition you can use multiserver arrays, and then store this information in the Active Directory directory:
- Configuration data.
- Policy information.
ISA Server can also apply access control for Active Directory users and groups.
- Network Address Translation (NAT); ISA Server can enforce ISA Server policy for SecureNAT clients.
- Virtual Private Networking; ISA Server can be configured as a VPN server to support:
- Secure gateway-to-gateway communication over the Internet.
- Secure client-to-gateway remote access communication.
You can use Point to Point Tunneling Protocol (PPTP) or Layer 2 Tunneling Protocol (L2TP)/Secure Internet Protocol (IPSec). PPTP, an extension of Point-to-Point Protocol (PPP), encapsulates PPP frames into IP datagrams to transmit data over an IP internetwork. To create and manage the tunnel, PPTP utilizes a TCP connection. When L2TP is used with IPSec, the highest level of security is assured. This includes data confidentiality and integrity, data authentication, as well as replay protection. IPSec protects the packets of data and therefore provides security on nonsecure networks such as the Internet.
- The following Windows authentication methods are supported by ISA Server:
- Basic authentication.
- NT LAN Manager (NTLM) authentication.
- Kerberos.
- Digital certificates.
- System hardening can be implemented through Windows security templates.
- If you install the ISA Server Enterprise Edition, you can extend the distributed nature of Active Directory directory services by configuring one or multiple enterprise policies and then applying the policies to arrays in the enterprise.
- ISA Server Web filters can examine and manage Hypertext Transfer Protocol (HTTP) and File Transfer Protocol (FTP) traffic over the gateway. The ISA Server Web filters are based on Internet server application programming interface (ISAPI).
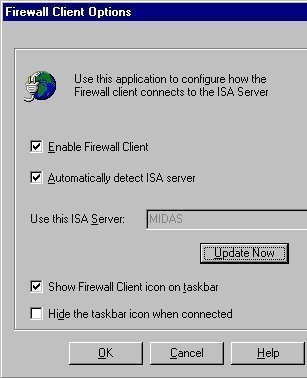
- ISA Server supports Web Proxy Autodiscovery Protocol (WPAD). This means that Firewall Client software running on ISA Server clients are able to automatically connect with ISA Server on the network.
- MMC administration can be used. The management interface for ISA Server is ISA Management, which is a MMC snap-in. You can integrate third-party products into the ISA Server management console.
- To improve performance, ISA Server uses the Windows symmetric multiprocessing (SMP) architecture.
- The Windows Quality of Service (QoS) capability is used by ISA Server to provide bandwidth control management.
- ISA Server records alerts to the Windows Event Log.
The Management Features of ISA Server
The management interface for ISA Server is ISA Management, which is a MMC snap-in. You can integrate third-party products into the ISA Server management console. ISA Management provides graphical taskpads and also a number of ISA Server wizards that can be used to manage your ISA Server environment.
The administrative tasks which you can perform through the ISA Server wizards are listed here:
- Use the Getting Started Wizard.
- Configure local, remote and client-to-server VPNs.
- Configure secure publishing.
- Specify a protocol rule.
- Create a site and content rule.
- Create a bandwidth rule.
- Configure a mail server behind ISA Server and define policy for the mail services.
- Implement system hardening.
You can use the same management interface for the ISA Server firewall and Web caching. Both the firewall and Web caching share the following:
- Reporting.
- Logging.
- Alerting.
You can also use the same access control policies to manage the ISA Server firewall and Wb cache server. You can though configure logging separately for
- Packet filters.
- Firewall service.
- Caching service.
The predefined reports that you can configure ISA Server to generate are listed here:
- Summary report, shows traffic usage.
- Web usage reports; shows Web usage information by common responses and browsers, and top user information.
- Application usage reports; shows application usage by incoming and outgoing traffic, destinations, client applications and user information.
- Traffic and utilization reports; illustrates total Internet usage by application, direction, and protocol.
- Security Reports; shows attempts to compromise network security.
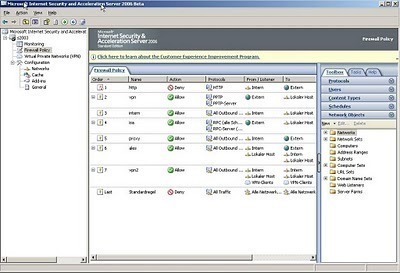
You can configure a policy for an ISA Server array or an ISA Server Enterprise. The different policy-based rules that you can configure are:
- Bandwidth rules; used to define priorities for requests, based on:
- Protocol definitions.
- Destination sets.
- Client address set.
- Content group.
- Required priority.
- Protocol rules; used to define which protocols clients can use to access the Internet.
- Site and content rules; used to define which sites and content can be accessed.
ISA Server rules are affected by policy elements. Policy elements pertain to a part or component of a policy. They are not created explicitly for each rule. Policy elements are predefined, and can be reused and customized.
The policy elements that you can define in ISA Management are listed here:
- Destination sets; IP addresses of specific computers, or computer names.
- Client address sets; IP addresses of specific client computers, or authenticated users and groups.
- Schedules; when a rule is implemented.
- Bandwidth priorities; define the priority level of a connection.
- Protocol definitions; includes port number, TCP or UDP, and direction.
- Content groups; MIME types or filename extensions, and content types that exist on the Web.

Follow Us!