Authenticating users in IIS is one of the initial steps in securing IIS. When a user attempts to access a website or an FTP site on an IIS machine, authentication is the process that verifies whether the user can indeed access the site. Authentication and permissions are closely coupled. After a user is authenticated, NTFS permissions determine whether the user can access folders and files and Web permissions indicate whether a Web or FTP client can read the website’s home or virtual directory.
The authentication methods that authenticate users in IIS 6 are listed below. Each authentication method authenticates users attempting to access websites. However, only Anonymous access and Basic Authentication can be enabled for FTP sites.
- Anonymous access.
- Basic Authentication.
- Integrated Windows Authentication.
- Digest Authentication.
- .NET Passport Authentication.
An authentication method for a website can be configured at the following levels:
- Web Sites node: The Directory Security tab is used.
- Specific websites: The Directory Security tab is used.
- Virtual directory: The Directory Security tab is used.
- Specific files: The File Security tab is used.
An authentication method can be configured for an FTP site at the following levels:
- FTP Sites node: The Security Accounts tab is used.
- Specific FTP site: The Security Accounts tab is used.
When more than one authentication method is configured for a website, virtual directory, or a file, the order in which the authentication methods supported in IIS are applied, is listed below:
- The Anonymous access authentication method is applied first.
- When the Anonymous access authentication method is not configured or supported, the Windows Integrated Authentication method is attempted, the Digest Authentication method is attempted next, and the Basic Authentication method is attempted last.
- No other authentication methods are available when the .NET Passport Authentication method is configured.
The Integrated Windows Authentication method is the standard authentication method utilized for authenticating users attempting to log on to a Windows 2000 or Windows Server 2003 computer or network. Integrated Windows Authentication is the recommended authentication method for authenticating users attempting to access web and FTP sites on IIS machines.
Integrated Windows Authentication consists of the following two methods of the authentication:
- The NTLMv2 method is used when the IIS machine is running in a network that contains Windows NT domain controllers or when the IIS machine belongs to a workgroup.
- Kerberos authentication is used when the IIS machine belongs to a domain – no Windows NT domain controllers exist.
The Integrated Windows Authentication method’s requirements are listed below:
- Internet Explorer 3.01 or later.
- Integrated Windows Authentication could experience problems with firewalls and proxy servers. Users may therefore need to configure Web clients to access the Web server through a tunneled connection, such as Point-to-Point Tunneling Protocol (PPTP).
Digest Authentication can only be enabled if Active Directory is used. Digest Authentication sends the user credentials over the network by utilizing an encrypted MD5 hash, and is therefore more secure than the Basic Authentication method.
The Digest Authentication method’s requirements are listed below:
- Internet Explorer 5 or later.
- Active Directory must be used with domain controllers running Windows 2000 or Windows Server 2003.
- Domain user accounts must be configured for users.
- Users and the IIS machine should belong to the same domain. If not, the same domain should trust them.
- The IIS machine must use the LocalSystem account when worker process isolation mode is enabled.
Basic Authentication is considered the most insecure authentication method that can be used for authenticating users in IIS because it uses a clear-text username and password. Basic Authentication functions over proxy servers and works with all browser clients. Basic Authentication is enabled for FTP sites by default.
With .NET Passport Authentication, .NET passports are utilized for authentication and authentication occurs via a single sign on method. When enabled, users’ credentials have unique Passport accounts. The Passport accounts are located on Passport servers that are connected to the Internet. Microsoft manages the Passport servers. IIS sends the user’s Passport information to the Passport servers for authentication when a user attempts to access an IIS website.
The steps that should be used to enable .NET Passport Authentication are listed below:
- Set up a site ID and all necessary Passport configuration settings on the IIS machine. Use the Passport Manager Administration Utility, msppcnfg.exe, to perform this task.
- Acquire a server certificate for the website. This certificate identifies the website when user authentication requests are forwarded to the Passport servers.
- Register the website with Microsoft’s Passport site.
How to Configure Authentication Settings at the Website Level
- Open the IIS Manager.
- Right-click a website in the console tree and select Properties from the shortcut menu.
- When the website’s Properties dialog box opens, click the Directory Security tab.
- In the Authentication and Access Control section of the Directory Security tab, click the Edit button.
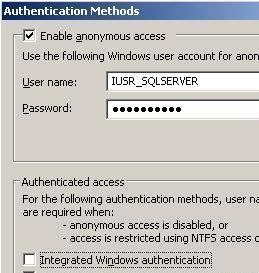
- The Authentication Methods dialog box opens. Configure the settings listed below on this dialog box:
- The website’s Enable anonymous access checkbox can be enabled or disabled. Anonymous access is typically used for public sites.
- The options that can be configured in the Authenticated Access area of the Authentication Methods dialog box are:
- Integrated Windows Authentication: This is the most secure option that can be used for authentication in IIS. Kerberos version 5 is utilized if the client browser includes support for the protocol. NTLM authentication is used when the client browser does not support Kerberos version 5.
- Digest Authentication For Windows Domain Servers: This option can only be enabled if Active Directory is used. Digest Authentication sends the user credentials over the network by utilizing an encrypted MD5 hash.
- Basic Authentication: This is the weakest authentication method available for IIS and should be utilized when no other authentication method can be used. Basic authentication uses a clear-text username and password.
- .NET Passport Authentication: When enabled, .NET passports are utilized for authentication and authentication occurs via a single sign on method.
- Click OK.
How to Configure an Authentication Method at the FTP Site Level
- Open the IIS Manager.
- Right-click an FTP site in the console tree and select Properties from the shortcut menu.
- When the Properties dialog box for the FTP site opens, click the Security Accounts tab.
- The Security Accounts tab has the following two checkboxes:
-
- Allow Anonymous Connections.
- Allow Only Anonymous Connections.
- To only enable the Anonymous Access authentication method, select both the Allow Anonymous Connections checkbox and the Allow Only Anonymous Connections checkbox.
- To enable both the Anonymous Access authentication method and the Basic authentication method, only select the Allow Anonymous Connections checkbox. Anonymous Access authentication will be automatically attempted before Basic authentication is attempted.
- To only enable Basic authentication, ensure that the Allow Anonymous Connections and Allow Only Anonymous Connections checkboxes are cleared (not selected).
- Click OK.
How to Configure Authentication Settings at the IP Address Level
Restrict Web access at the IP address level by only allowing users to access a site that is using an IP address from a predefined list of approved IP addresses.
To do this:
- Open the IIS Manager.
- Right-click a website in the console tree and select Properties from the shortcut menu.
- When the website’s Properties dialog box opens, click the Directory Security tab.
- In the IP Address and Domain Name Restrictions section of the Directory Security tab, click the Edit button.
- The Address and Domain Name Restrictions dialog box opens.
- Using the dialog box, specify that all computers are granted access or specify those computers that should not be granted access by listing their IP address or domain name.
- Click the Add button to include particular users’ IP addresses in a list.
- Click OK.


Ensest Hikayeler
Great post, i need this issue, you explain very clearly